Introduction
This book is dedicated to all those good people who give their time and energy, and sometimes in some places, their freedom or even their lives, to do something they truly value. This is a book on anonymity and privacy in this lush forest full of data hunters called the internet.
Every species in this jungle has one thing in common: they all have data they want to protect. Even if they don't want to admit it, even if they say they have nothing to hide—and maybe they're right—I don’t hide my credit card credentials, but I never want anyone I don’t trust to have their hands on them. And that’s what privacy is.
Privacy is a human right, and nobody should have the right to take it away from someone else. Unfortunately, we live in a world where our rights mean nothing. Companies, doxxers, governments, spy agencies—everyone violates our right to privacy every day. They won’t stop; they profit from our data. Our data is the foundation of their businesses. We are the ones who need to stop handing over our data (to some degree at least, without making our lives miserable and unnecessarily hard).
Some might call this need for privacy paranoia, but protecting yourself and your loved ones from future harm is not paranoia. Think of privacy as insurance. You might trust your government today, you might trust your messenger with your messages, you might trust Google with your whole life, but remember, Satan was once an angel too. Anyone can turn evil; any government can become corrupt and dictatorial. You wouldn’t want them to know every single second of your life when they do.
Privacy nowadays is not possible without security. Your data needs to be secure to authorize those you want to have access to it. You should expect that everything you put online will be read and opened one day. All you can trust with your data is encryption algorithms and the mathematics behind them that ensure their security and reliability. However, even the most secure encryption algorithms might be broken one day, and it's good to keep that in mind.
Privacy and security are also the building blocks of anonymity. You will need both to stay anonymous. Anonymity is when people see what you do, what you want them to see, but they can't know who is actually behind those actions. It is similar to privacy, but in privacy, they know who you are, but they don’t know what you’re doing.
This book is free, not just in the sense that it costs nothing to read, but free as in freedom. It is a side project of mine, written in my free time under the CC BY-NC 4.0 license. This license allows anyone to share and copy it in any medium and make changes to it, as long as they give credit to the author and indicate the changes they’ve made. Additionally, this license does not permit commercial use.
I’m not doing this for profit; if I wanted money, I would have worked for it. This book and all other projects of mine are driven by my passion for creating free content and software that I think could help others who need them. However, I accept and greatly appreciate donations, as they allow me to spend more time on what I value and not worry as much about working another job that I don’t like just to make a living. If you find my work helpful or want to support what I do, please check the donation section of this book.
This book isn’t meant for criminals, terrorists, racists, or anyone who wants to hide their wrongdoings. It is for human rights activists, those fighting for freedom in places where it is not allowed, and those contributing something good to society rather than tearing it apart. It’s for the heroes who need to wear a mask to protect themselves and their loved ones, not for the supervillains.
Chapter 1
The Dunning-Kruger effect shows that when you start learning a skill, you often have very high confidence in yourself and your skill because of how little you know about what you're doing. As you actually start learning, your confidence drops, and over time, as you begin to master the skill, your confidence increases again, but this confidence is now backed by your actual skill. The same applies to privacy and security. Initially, when you start, you might think that opening an incognito tab makes you safe, and nobody knows what you're doing. But as you learn more, paranoia can creep in because you realize how vulnerable you actually are. However, over time, you will build confidence and actually feel safer, and this time, you are genuinely safer than before.
In the first chapter, the focus will be on uncovering some privacy and security myths that most newbies in the world of privacy believe in, which can actually make your privacy worse by making you more unique while providing no actual benefit.
I have no enemies
The first myth, and apparently the biggest one in the world of privacy, is what I call the "I have no enemies" phenomenon or what you might know as "I have nothing to hide."
As I mentioned in the introduction, even if we don’t have things to “hide,” we certainly have things we want to protect. Or maybe it’s not about us; perhaps people we know and care about have things to hide, and we could be the weak link in their privacy.
You and I don’t have enemies today; we don’t have things to hide today. But can we say for sure that this will be true in five or ten years? Certainly not. We don’t and can’t know what will happen. Our current privacy can serve as insurance for what may happen later.
Imagine someone managed to gather your personal information and used it for illegal activities. Would it be harder to convince the police or FBI that you didn’t do it than to protect your personal information in the first place? Or maybe, ten years later, if Google turns evil and acts as a “terrorist detection tool” for the government, and while traveling with your wife and kids, they pull up your emails, search histories, and ad suggestions. If, because of your search on explosives last year for your kid’s birthday and the ad suggestions you received, you are flagged as a terrorist, you could end up spending the rest of your life on a watchlist.
But I assume if you are reading this book, you probably understand the importance of privacy, especially in this day and age when it is one of the least respected human rights. However, we all can change that. The blame for this situation falls on governments, doxxers, companies, and those so-called "national security agencies." Nevertheless, the responsibility to make things right is on us. We should protect our privacy.
I'd just go incognito
If you ask someone who's not familiar with how the internet works what they would do to become totally anonymous online, they might say, "I'd just open incognito mode." This is probably the most common myth in the privacy world among those who aren't tech-savvy—that incognito mode means no one will be able to track them or see their activities online. But that's far from reality. All incognito mode does is prevent the browser from saving your history and logins.
Your ISP still knows what you're doing, the websites you visit know your IP address, and you remain unique and fingerprintable. Incognito mode does have some privacy benefits, particularly if you use someone else's computer; in that case, you wouldn’t want your cookies, search history, or logins to be stored on their device. However, it doesn't contribute much to your overall privacy or security beyond that.
To hide your activities, you would need something that encrypts your requests and reroutes them to the destination you want to go, such as a secure proxy, an SSH tunnel, or a VPN. However, the sites you visit can still fingerprint you and track you across other websites. I’ll cover these in depth in the next chapters.
VPNs are Anonymous
This is kind of the biggest myth in the privacy and anonymity world: that if you use a VPN, nobody will know what you’re doing, and you’ll become totally anonymous. But that’s completely wrong. See VPNs as shifting the trust from your ISP to your VPN provider. When you connect to your VPN, you are now letting them see what your ISP was seeing before.
Also, they don’t do a good job at hiding your real IP. With most VPN companies, a court order can compel them to hand over all the logs and data they have on you, and usually, they have a lot. There are some exceptions, though; some companies like Mullvad, ProtonVPN, and Windscribe have built their companies based on the privacy of their users. They can be signed up for anonymously, paid with cash or crypto, and they don’t log user traffic and activities. But still, that doesn’t make them an anonymity tool.
Even if your VPN provider doesn’t log anything, the data centers hosting their servers surely will. Another issue is that VPNs are vulnerable to traffic analysis. VPN traffic can be analyzed to find patterns that indicate the source and destination of your traffic, and that is fine; VPNs aren’t meant to be an anonymity tool after all.
Another problem with VPNs is fingerprinting. With Tor, you have the Tor Browser, which is designed to make all Tor users look identical. But with VPNs, you’re the most unique person on this planet, especially if you have a browser that is modified in any way or if you’re using an operating system like Linux or BSD. Smallest changes can make you super unique when it comes to fingerprinting, and that’s what you don’t want for anonymity. For privacy, though, that would be fine. You can safely use a hardened Firefox, for example, for your personal usage, like watching YouTube and paying your bills. That’s actually a good move. In that scenario, you don’t need to look like everybody else; you can be unique. I’ll cover fingerprinting more in the next chapters.
If you want to keep your anonymity, you should use tools specifically built for it, like Tor (and the Tor Browser). What Tor does is what its name stands for: The Onion Router. It works like an onion; it encrypts your data in three layers. As the data passes through each Tor relay, one layer of encryption is removed, revealing the address of the next relay in the chain until the data reaches the final destination. When browsing the clearnet with Tor, your last relay will be a node called the exit node. The exit node can see the data inside your packet, but it won’t know for sure where the origin of the packet is. To trace a packet back to its sender, all relays that your traffic passes through must be controlled by one person, and that’s very unlikely and costly to implement. When you browse websites hosted on the Tor network, your data is end-to-end encrypted with the website’s public key (the website’s address is the public key, and that’s why Tor addresses are so long and hard to memorize). So nobody in the middle can open the traffic; they will just pass it through until it reaches its destination.
There are other anonymity tools as well, such as Lokinet (which is the newest) and I2P. Both are technically more anonymous than the Tor network, but technicality isn’t everything. I2P and Lokinet both have very limited nodes compared to Tor, which makes the network more vulnerable. Additionally, neither provides a browser like the Tor Browser to prevent fingerprinting of users. For now, the best option is Tor, both because of its proven track record over the years and its considerable number of volunteer nodes and relays, and also because the Tor Browser does a great job at making Tor users identical to each other when using the Tor network.
Something to keep in mind when using the Tor Browser is that you shouldn’t modify anything. Leave it as is; don’t install plugins or tweak it. The Tor Browser is meant to have similar fingerprints to other Tor Browsers, and even the smallest changes might make you the most unique person on the Tor network.
I'm using a strong password
Another myth that I see a lot of normies believing is that they have to have a strong password—something random and hard to memorize. Having strong passwords is a must, but having a strong password for everything not only doesn’t contribute much to your security but also makes you very vulnerable.
Imagine you use your strong, complicated password for every site you’ve ever signed up for. If one of these sites didn’t store your password properly and they got hacked, and their database went public, now anybody can use that same password for any other website or service you’ve signed up for, and they’d log in.
Instead of bothering with memorizing a really hard password, you should use a password manager, either something locally stored like KeePass or something online like Bitwarden.
Those password managers that store passwords locally are obviously more secure than the online ones, simply because if anyone wants to get access to their database, they’d have to gain access to your computer. I’m not saying it’s not possible to gain access to your computer, but Bitwarden’s servers might be far more targeted than your personal device. Other than that, they’re both fully encrypted. Even if something got leaked someday, your data will be securely stored and nearly impossible to access, at least with the tools and computers we have today.
Your password manager can then be accessed using a passphrase (not a password). Passphrases are way more memorable while being a lot more secure. A passphrase can be something like: Name-Seat-Look-Chair-Plane7-Stree7—just 6 words, one punctuation character, and 7s instead of the letter T. Compared to a password like *&(*747983HJGHgdgsutpshlnb, the passphrase will be more secure while being memorable.
Big Tech is evil
There is this idea, even among people who are not normies, that big tech companies are evil, and that they have bad security and bad privacy. That might be true for privacy, but not much for security. Companies like Google and Microsoft probably have good security, but we can never be sure.
This is because they’re not open about how they have implemented things. We can’t see what they do to protect our data, and that’s what makes them untrustworthy. A company like Signal has its server, client, and encryption schemes open-sourced for the public. On the other hand, something like Telegram only has its client open-sourced, and that’s it. We don’t know much about the server or even their encryption scheme, which they brag is unbreakable. In this situation, we say Telegram is not good for its purpose, which is messaging people. It is not secure.
However, in the case of something like Google Drive, which gives you a reasonable amount of free cloud storage, you can use it. If you already have a Google account associated with your identity, you can use Google Drive to upload some encrypted data that you don’t have space for. Just because it’s Google doesn’t mean that it’s pure evil, and there can be uses for it. You can use Google once you are self-conscious of your privacy.
Although every day more and more privacy-friendly alternatives are coming out, so in the near future you might not need to use Google or other companies like it.
Open-source means private
Yes, open-source software is more transparent than proprietary software and has the potential to be more secure and private, but transparency and potential alone don’t make them more private or more secure. You need to look for independent audits of the software you are about to use. Also, being proprietary doesn’t mean they’re less safe. Look for the reputation of the software and the maintainers of it and whether they are audited or not.
These were some of the most common myths about privacy and security online. There are endless myths that people believe in. In these situations, we should be logical rather than biased. We need to plan out what we need to do, what is worth our time and energy, and the next chapter is about that—about threat modeling and common threats that you need to know before you start designing your threat model.
Chapter 2
Imagine you're playing Minecraft, and you have respawned somewhere random on the map. You don’t have the geolocation of the house you built. It will be really annoying and time-consuming, or even sometimes impossible (you might give up due to frustration), to find your home in the game if you don’t know where and in which direction to go. You run out of food and energy, and there will be nights with all the mobs, zombies trying to attack you, skeletons shooting arrows at you, and creepers blowing themselves up right beside you. But if you had the X, Y, Z coordinates of your house and the direction you needed to go, you could have gotten there before nightfall and avoided all that hard time fighting mobs and getting nowhere.
In this book, I’ve planned to explain more advanced topics as it progresses. So the first chapter debunked some common myths about privacy and security, and in this chapter, things get a little more actionable. This chapter is all about threat modeling, as I believe it is the most important step to take when you start your privacy journey. Otherwise, you’ll spend a lot of time, stress, and hard work, and all the effort will be of no benefit for your personal needs.
Having a threat model can be the equivalent of having the location of your house in Minecraft written down on paper. Whenever you go far away from your home, you know where to go to get back. In the case of privacy and security, you will know what threats you personally face, what you want to protect, and take actions based on that, rather than blindly using Tor on Whonix OS for no actual reason and potentially making your life harder and even your privacy worse in the process.
There's nothing called full security
Nothing can be fully secure, fully private, or fully anonymous. When it comes to threat modeling, you need to make sacrifices. You should see what matters the most and work on those areas rather than wasting time trying to make everything private and secure, which is impossible.
A threat model is a list of what threats are most likely to happen. You can't protect yourself from every threat, but you can work on protecting yourself from those that are most likely to happen.
For example, for a rapper, the most likely threat could be their music getting leaked. When designing your threat model, you should address these questions:
- What do I need to protect the most? In the example of the rapper, the unreleased music would be the answer.
- Who do I need to protect it from? For the rapper, that could be online hackers and those who are physically with him and have access to the songs.
- What are the chances of it happening? For the rapper, if he's famous enough, it's quite likely.
- What will happen if I fail? For the rapper, that could cost him financially.
- What can I do to protect it? For the rapper's example, he could use encrypted hard drives and restrict access to others to prevent human errors.
What do I need to protect the most?
To answer this question for yourself, you need to first list what you value the most. It could be your digital assets, like your cryptocurrencies, the information you have, like your emails, your contacts, your messages, or some files that are important to you. Whatever you value, write them down.
Make your list like this: what data it is that you're protecting, how and where you're keeping it, who you want to allow to have access to it, and what can be done to prevent unauthorized access to it.
When you write your list, prioritize it based on the most valuable to the least valuable data. Then you can take a step forward.
Who do I need to protect it from?
It can be anyone and anything; it's up to your personal situation. For an activist, for example, it could be the government. For someone who protests against fascism, it could be neo-Nazi hackers and doxxers. For a business, it can be their competitors.
Try making a list of those who might be interested in getting their hands on your assets or data. Your list can include individuals, a federal agency, a corporation, a doxxing group, a cult, anything—you know it better.
This list can help you see what and who you're standing against, what they can do, and what costs they might be willing to pay to get their hands on your data. It helps you see more clearly and realistically.
What are the chances of it happening?
Not everything that might happen will happen. Write down the threats that you think are going to happen, as many as you can think of, and then rate them based on their probability of happening. Is it highly probable to happen? Is it rarely going to happen? Is it even possible to protect your data against it?
For example, you might get struck by lightning when it's raining and die, but how probable is that? Would you find an insulating shelter until the rain ends? No, because there's a low chance of it happening. Or you might crash your car every time you get behind the wheel to drive, but do you stop driving? No. Or you might get shot if you go to a gang war zone, and you probably won't, because it's quite likely to happen. The same goes for your threat modeling; you need to rate the threats based on their probability of happening.
What will happen if I fail?
Then you need to see what the consequences of failing to protect your data are. For example, for an anti-fascist protester, if doxxers put his home address and all information online, it could pose physical threats to him. Or, if a company fails to protect its data, hackers or competitors might corrupt all the company's data and drive it toward bankruptcy. On the other hand, if I, who sends memes to my friends on Telegram, have my messages read by someone, probably nothing horrible will happen to me.
You need to write down what the attackers might want to do when they get their hands on your data. Will the harm they cause be so little that you wouldn't bother? Or is it so significant that it could be life-threatening? You need to address these questions.
What can I do to protect it?
Then you can move on to doing your research, seeing what can be done to protect that data, what costs will come with it, and how much it will make your life harder. Are you willing to take the effort?
For example, if you have cryptocurrencies, you can see how you might protect your assets. You might need to implement multi-signature wallets or store your assets offline on a safe and dedicated machine with encryption and no additional software on it.
Then you take action
After you design your threat model, you can move on to taking action toward it. In the example of cryptocurrency assets, you can start by backing up your assets on paper, putting it somewhere safe, using an offline and audited wallet, downloading your own blockchain instead of relying on nodes run by others, and even buying a dedicated machine specifically hardened for this need and purpose.
You might create a checklist at this point to make sure you don't forget anything and implement all the actions you think would keep your data secure.
Common threats when threat modeling
Different threats require different actions; there is no action you can take to protect yourself from all of them. And that's fine—you don't need to. That's why you designed a threat model: to take actions on the most probable and most consequential threats based on your own personal situation.
Your threats might not be among this list of common threats. They might require unique strategies to protect yourself against. Again, you should act on your threat model. These are some concepts that I will refer to in this book, especially in this chapter:
- Anonymity: Separating and protecting your real identity from your online activities, protecting yourself from anyone/anything wanting to take your vigilante mask and see your real face.
- Targeted Attacks: Protecting yourself from hackers, doxxers, government agencies, etc., that are specifically trying to get their hands on your data.
- Passive Attacks: Protecting yourself from attacks that target a large group of people, such as when a company gets hacked and their data breaches to the public, or from malware and scammers targeting thousands of people.
- Supply Chain Attacks: Attacks that happen because of a vulnerability in a dependency of a trusted program, like the Linux distros getting backdoored because of a backdoor in xz utils (CVE-2024-3094) in 2024.
- Service Providers: Protecting your data from service providers, like your ISP, usually through end-to-end encryption of your communications.
- Mass Surveillance: Protecting yourself from surveillance systems that target the mass population, usually done by governments, but also includes websites that track you across the web.
- Big Tech Surveillance: Protecting yourself from big tech companies that profit from tracking you on the internet and selling your data for advertisement, like Google, Facebook, etc.
- Public Exposure: Limiting the data available about you publicly on the internet, for example, your personal data indexed by search engines, etc.
- Censorship: Bypassing digital censorship or avoiding being censored when using the internet or putting something out on the internet.
Anonymity vs Privacy
Anonymity is totally different from privacy, but privacy is required to achieve anonymity. Anonymity is when Daredevil goes out at night to fight the Russians working for Wilson Fisk—they don't know that Daredevil is Matt Murdock, but they know what he does. Matt Murdock has untied his personal identity, which is a blind attorney, from his vigilante identity, which is this badass dude in a black and red suit fighting crime in Hell's Kitchen. Matt Murdock is anonymous when he's Daredevil, and Wilson Fisk and every other criminal he has fought are the attackers who would love to unveil his identity and find out who's behind the mask.
In this example, Matt Murdock has used privacy to achieve that anonymity. He has separated his identity in a way that nobody would be suspicious of him being Daredevil. He pretended all these years that he can't see anything, can't even walk without his cane, and even if he was injured, he would say that he fell down some stairs. That's the privacy there protecting his anonymity. He decided to let people see this side of Matt Murdock, not the Daredevil side of him.
The same thing applies in the online world, but here the tools are different. The masks are digital tools using encryption and onion routing, but the concept is the same. If you're some kind of vigilante like Matt Murdock, you probably need to protect and separate your real identity from your vigilante identity.
Targeted Attacks
Daredevil was targeted too; all of Hell's Kitchen criminals were after him. So he both needed to protect his identity and anonymity while protecting himself against targeted attacks from one of the most powerful villains of New York, the Kingpin. But who else might be in the situation of Daredevil? The whistleblowers, the activists, and the protesters. But they need different tools than Matt Murdock. They might need the Tor browser rather than a mask; they might need E2EE tools to communicate and store data rather than an indestructible suit made by Melvin Potter.
But if you think the NSA, CIA, and other agencies are after you, you can't run from them forever. You might be able to fake your death and live in a submarine, but they will probably find you. This usually categorizes as those threats that you rather not bother about because of how difficult it might make your life. Also, it is quite rare to be that targeted. Usually, those targeted by the NSA have the support of another corrupt government.
Passive Attacks
This kind of attack affects most people of Hell's Kitchen, from Foggy Nelson to Frank Castle, even the people of Gotham City. It affects the villains and the heroes, from Batman to Harley Quinn. These attacks are usually toward large groups of people, like malware spreading on the internet. When WannaCry spread on the internet, it affected anything that had that vulnerable version of Windows. It didn't choose.
This kind of attack, in my opinion, is most probable for the majority of people. We all have signed up for many websites in our lifetimes. A data breach in one of them would be really likely and can definitely affect us if we haven't taken any precautions.
Supply Chain Attacks
Supply chain attacks can target even the most trusted programs by attacking other programs that our programs are built on. Supply chain attacks are sometimes targeted at businesses or governments, but they can affect the mass population in the process. These attacks are hard to prevent; they require time and energy to audit and test every dependency on the chain to be sure, but we can't be certain. There are always flaws—nothing can be fully secure.
So, how can these attacks be performed? There are a lot of ways; here are some common ones:
- Someone with enough power and a high enough position in a company or developer team can have the authority to add malicious code to a software.
- In the open-source world, someone can contribute malicious code in a way that it gets added to the codebase unnoticed.
- The author and maintainer of a library or dependency can decide to inject a backdoor in the code.
Minimizing the Risk
How can we minimize the risk? Well, it can't be fully eliminated, that's for sure. But there are ways:
- Software and services from big companies like Google usually have a good reputation and better security than software developed by a small team or an individual.
- Checking the commits, changes, and contributors in the case of open-source software.
- Frequently checking for known security flaws in software.
- Using independently audited software.
- Sandboxing and isolating to minimize the impact of possible attacks.
Service Providers
Your ISP can see all your traffic, like the Joker putting a GPS on Batman's Batmobile. The Joker knows where Batman is going and can log those movements as well. However, thanks to TLS and HTTPS, the data that ISPs can see has become limited. They can know the IP address and the Server Name Indicator (SNI) of your traffic and the DNS queries, but there are fixes. We can encrypt DNS, encrypt the Client Hello, and SNI, so all your service provider would see is the destination IP and timestamps if TLS is enabled for that website or service.
You can also shift the trust from your ISP to a VPN provider that doesn't log your traffic and allows you to sign up anonymously, such as Mullvad or Proton VPN. But remember, this is just shifting the trust, not eliminating it. For that, there are other tools, such as Tor, which ensures that no one in the middle can see where you're going and what you're doing (if you use websites on the Tor network and not the clearnet).
Using encrypted DNS is also shifting the trust; the DNS server still knows who you are and when and where you wanted to go. Luckily, Tor has its own DNS as well.
Mass Surveillance
David Liberman, also known as Micro, was an NSA analyst and hacker who, when he tried to expose the CIA's drug trafficking in Afghanistan, was "killed" by a corrupt Homeland Security agent. However, he survived. He gained access to all CCTV cameras and everything that these government agencies had access to, so he could find Frank Castle, aka the Punisher, to help him kill all those who were a threat to his family so he could get back home. At least, that’s what I remember. The movie is not the point. This kind of act—spying on all people, spying on all internet traffic, logging every packet—is what is called mass surveillance. It affects everyone.
Governments usually justify this by saying that they're fighting terrorism, which is not true in reality. It has little to no effect on crime, and some governments use it for social credit systems.
Big Tech Surveillance
There is another kind of mass surveillance that is not done by governments or agencies; it is done by big tech companies like Google and Facebook. Being the biggest tech companies with the most internet users, they gather and collect a huge amount of data, sometimes even more than the government would do in some countries.
This kind of mass surveillance is different from that done by governments. The companies don’t deny it or claim it’s for stopping terrorism or national security; they simply do it to sell the data they gather.
They make tons of money from your data by using it for advertising. They track you across the internet. But there is no guarantee that it won't go beyond just money and advertising. They might work with government agencies in the future as well.
Public Exposure
When I was 8 years old, I created a personal website for myself, which had my name, email, and phone number on it. It took me months, going back and forth with Google and the blogging website, to take it down from the search engine results. This is what public exposure is: the data that is publicly available about you online. It can even be put out there by yourself when you didn't care about privacy. It is quite hard and sometimes impossible to take it down. In fact, it is always impossible to truly delete something you have put out there on the internet. That's why you should set your mindset to assume that if you say something, post something, or share something, it might stay on the internet forever. Even if it's encrypted, you need to assume it will be read one day—maybe not in your lifetime, but eventually.
Prevention is the best treatment. The best way to keep your data private is to not make it public to start with. Keep in mind that nobody will call the cops on you for not signing up on Instagram with your real identity. It's the internet; you're not signing up for the military or opening an account at a bank. You don’t need to use your real name, phone number, and home address on the internet. Nobody needs to know these things about you. Keep your real phone number for those you know personally, not for every troll, doxxer, or anyone who might use the internet. The same goes for your real name and other personal details.
Avoiding Censorship
Sometimes you just need privacy and security to avoid censorship, whether it is applied by a government, a platform like Twitter, or a Matrix server administrator. Most of us, including myself, hate censorship. Censorship holds society back from growth; it's like shutting off innovation, creativity, and new ideas. It is usually imposed by those who need to protect their empires by force because they themselves know how wrong they are.
In this scenario, privacy tools like VPNs, proxies, encrypted DNS, and Tor can help you bypass censorship. Privacy-friendly platforms like Mastodon, which allow you to host them yourself, enable you to speak freely without someone like Elon Musk getting mad at you.
The journey begins...
These were some of the common threats and ways to design your threat model. It can vary based on your unique situation; you need to address your own personal needs when it comes to threat modeling. But it's not something you should skip; otherwise, you would be lost and waste time and energy on things you don’t need. That was how I started my privacy journey. I didn’t design a threat model; instead, I tried to make myself bulletproof from every possible attack. Not only did I waste a year of my life, but I also gave myself long-lasting anxiety and paranoia for no reason, all because I didn’t plan out who I was protecting my data from.
This concludes this chapter. In the next chapter, I will cover operational security, which, though not technical, is one of the most important aspects of privacy and anonymity online. Operational security, or opsec, involves preventing sensitive data from falling into the wrong hands.
Chapter 3
In 2012, the FBI caught a hacker with the nickname w0rmer after he hacked several U.S. law enforcement websites and released their data online. You might think there was a big and complicated operation to catch this hacker, but no, w0rmer just had bad opsec. He handed the FBI his exact geo-location simply because he replaced the FBI's database with a picture of his girlfriend from the neck down in a bikini, holding a sign saying "PwNd by w0rmer & CabinCr3w, <3 u BiTch's!" It wasn’t that they figured out who the girl was from that picture; w0rmer forgot to (or didn’t care to) erase the EXIF metadata of the picture. The FBI looked at the picture, and in its metadata, they found that it was taken with an iPhone 4, with GPS coordinates of an outer-Melbourne suburb. w0rmer had overshared his location through a picture.
The electrical tape on your webcam and your Tor browser inside Whonix OS can't help you if you share too much about yourself, if you over time tend to expose your real identity piece by piece. Having good opsec often means having control and awareness of what you're sharing when talking to people or when posting online.
Identify the sensitive data and information
The first step in improving your OPSEC is identifying the data that is sensitive to you. To do this, you need to refer to your threat model. Assess what threats are common and which data would have the most severe consequences if it falls into the wrong hands. Then, prioritize the information based on the severity of the consequences.
Having this plan in place would reduce the unnecessary caution you need to take. Being overly cautious about everything you say or share can consume a lot of mental energy and increase the chance of slipping up. By focusing on what is sensitive based on your unique situation and threat model, you can minimize the mental effort required to maintain OPSEC.
Common Sensitive Information
These are some of the most common types of sensitive information that an individual might want to protect, but it all depends on your unique situation and whether these match your threat model.
-
Personally Identifiable Information (PII): Information that can uniquely identify an individual.
- Full legal name: Your complete legal name as recorded on your identification documents.
- Addresses: Your physical location where you live or work.
- Phone numbers: Numbers assigned to your phone lines, including mobile and landline numbers.
- Email addresses: Email accounts that are tied to your personal identity.
- Date of birth: The date you were born, typically used for verification purposes, and can be used to narrow down your identity.
- National identification numbers: Unique numbers issued by governments to identify citizens of a country, but even something like a library card number can be sensitive if tied to your personal identity.
-
Financial Information: Data related to your financial transactions and accounts. Some of this information can be PII as well.
- Bank account numbers: Unique numbers assigned to your bank accounts for transactions.
- Credit/debit card numbers: Numbers found on your payment cards used for purchasing goods and services.
- Payment information (PayPal, Venmo, etc.): Details used to process financial transactions through payment services, like your PayPal email or Venmo username.
- Financial statements: Documents detailing your financial transactions and balances.
- Tax information: Details related to your tax filings and records.
-
Account Credentials: Information used to access online accounts.
- Usernames
- Passwords
- Security questions and answers: Predefined questions with answers used for account recovery.
- Two-factor authentication (2FA) codes: Temporary codes used in conjunction with passwords for additional security.
-
Digital Footprint and Metadata: Information that can be used to trace your online activities.
- IP addresses: Unique numerical labels assigned to your devices on a network.
- MAC addresses: Hardware identifiers assigned to network interfaces.
- Browser fingerprints: Unique configurations and settings of your browser that can be used to track you.
- Device information (model, OS, etc.): Details about the devices you use to access the internet.
- Geolocation data: Information about your physical location derived from your devices.
- Cookies and tracking scripts: Small files and code snippets used to track your activity online.
-
Communication Content: The actual content of your communications.
- Emails: Digital messages sent through email services.
- Text messages: Short messages sent via SMS or messaging apps.
- Social media posts: Content shared on social networking platforms.
- Chat logs: Recorded conversations from instant messaging services.
- Voice and video call recordings: Audio and video data from calls made over VoIP services.
-
Behavioral Information: Data about your online behavior and habits.
- Browsing history: Record of websites you have visited.
- Search queries: Terms and phrases you have searched for on search engines.
- Online shopping habits: Patterns and preferences in your online purchasing behavior.
- Social media activity: Your interactions and engagement on social media platforms.
- Writing style: The way you write or speak.
- App usage patterns: Information about how you use mobile and web applications.
-
Professional Information: Work-related information.
- Employment details: Information about your job and employer.
- Work-related documents: Files and records related to your professional activities.
- Business contacts: Information about your professional network.
- Project information: Details about the projects you are working on.
- Client data: Information about the clients you interact with in a professional capacity.
-
Biometric Information: Unique biological traits used for identification.
- Fingerprints: Unique patterns of ridges and valleys on your fingertips.
- Facial recognition data: Digital mapping of your facial features.
- Voiceprints: Unique characteristics of your voice used for identification.
- Iris scans: Detailed images of the colored part of your eye.
-
Personal Preferences and Opinions: Information about your beliefs, preferences, and opinions. This can be critical if you live under a dictatorship or in a highly repressive environment.
- Political views: Your beliefs and stances on political issues.
- Religious beliefs: Your faith and religious practices.
- Sexual orientation: Your sexual preferences and identity.
- Health information: Data about your medical history and current health status.
- Memberships in various organizations: Affiliations with clubs, societies, and other groups.
Protect the Sensitive Information
Now that we know some of the common sensitive information in OPSEC, we can move on to approaches to protect this information. These protections also vary greatly based on your personal situation and your unique threat model. Always take a look at your threat model.
Personal Identifiable Information (PII)
- Encrypt files and documents containing PII using strong encryption algorithms such as AES. Never create your own encryption; use an algorithm that has been proven to be secure and an implementation that has been audited.
- Minimize the collection and retention of unnecessary PII. Provide your PII only if you have to, and there is no other way around it. If you have the chance to avoid providing your PII and use a pseudonym or a fake identity, do it.
- Store physical documents containing your PII, like your passport, in a safe place with surveillance systems like CCTVs.
Financial Information
- Use secure connections (HTTPS, for example) when accessing your bank website or any other financial website.
- Regularly monitor your financial accounts for unauthorized access and enable warning features if your bank provides them.
- Enable transaction notifications for all transactions so you are alerted to any suspicious activity on your accounts.
- In the case of cryptocurrencies, use cryptocurrencies that are decentralized and provide anonymity, like ZCash and Monero. Most cryptocurrencies aren't anonymous; they're pseudonymous. Nobody would know the owner of the address, but as soon as you spend the money in the real world, it will be traced back to your real identity. This is not true for privacy coins like Monero.
Account Credentials
- Use an audited and reputable password manager to store your passwords and account credentials. Never try to remember your passwords or, worse, use the same password everywhere. Each website should have its unique password to prevent unauthorized access to other accounts if one account's password gets leaked.
- Enable 2FA whenever possible to add an additional layer of security to protect your accounts. You can use physical devices for 2FA or audited open-source apps for TOTP codes. Also, make sure you protect your 2FA credentials as well as your passwords.
- Never share your account credentials via email or unencrypted messaging platforms. If you must share them, use encryption or a secure messaging app like Signal and enable auto-delete for the message.
- Periodically review and update account passwords. You can also sign up for services that check the dark web or database breaches for your account and notify you if your account is found in these breaches.
Digital Footprint and Metadata
- Use a pseudonymous VPN or Tor (highly depending on your threat model) to mask your IP address by encrypting and rerouting your internet traffic.
- Harden your browsers or use Tor Browser to limit the collection of browser history, cookies, and other metadata. You can also configure your browser to minimize its fingerprintability, but using Tor Browser is generally better if you want to avoid fingerprinting.
- Use privacy-friendly search engines like DuckDuckGo and StartPage or host your own search engine like Searx.
- Disable location services on your device when you don't need them. The location, when enabled, can be stored in the pictures you take as well.
- Remove the EXIF metadata from pictures before sharing, or use a camera app that does this by default.
Communication Content
- Always use end-to-end encryption when communicating. Use messaging apps like Session and Signal, which have strong encryption and store little metadata.
- Use encrypted emails like Tutanota and ProtonMail or use PGP to encrypt your emails before sending. However, emails will always have a lot of unencrypted metadata.
- Avoid sharing sensitive information over unencrypted channels, such as public Wi-Fi. Ensure your communication channels are encrypted.
Behavioral Information
- Use privacy-friendly search engines to minimize tracking of online activities. Also, disable search suggestions in your browser to prevent leaking your searches to third-party services.
- Regularly clear browser history, cookies, caches, etc., to ensure you don't leave any traces of your activities on your browser. Alternatively, use Tor Browser if it aligns with your threat model.
- Review and adjust privacy settings on social media platforms and websites you sign up for to minimize the collection of personal data.
Professional Information
- Encryption overlaps here as well, so encrypt work-related documents and files using strong encryption, just as you would for other data.
- Use secure, encrypted collaboration tools for sharing sensitive work-related information.
- Implement access controls and permissions to restrict access to confidential work data.
Biometric Information
- Again, store biometric information encrypted using a strong and known encryption algorithm and implementation.
- Limit the collection and storage of biometric data to what is necessary for authentication purposes. If possible, avoid using biometric data for authentication.
Personal Preferences and Opinions
- Be cautious about sharing personal preferences and opinions on public platforms, or at least avoid using your real name.
- Adjust privacy settings on social media to limit the visibility of personal preferences and opinions.
- Use pseudonyms or anonymous accounts for discussions on sensitive topics. This can sometimes be crucial depending on where you live.
Effective OPSEC goes way beyond implementing some techniques; it's about shifting your mindset. It demands a heightened awareness of the information we share and a commitment to continuous learning and adaptation. The threats are always evolving, and these techniques may become deprecated, but if you set your mindset to the fact that what you put online may stay there forever and will be read someday, you will find the techniques.
"If you know the why, you can live any how."
― Friedrich Nietzsche
The next chapter will be about privacy and security's essentials. Now that the myths are busted, the roadmap is ready, and the mindset is set, we can move on to the essentials of the privacy world: the tools and techniques that can be used to enhance your privacy.
Chapter 4
Continue imagining that you're playing Minecraft, like in Chapter 2. Now that you know the game, you have the locations written down, and you have some wood and a crafting table at your disposal, you can build tools like wooden axes, shovels, swords, a bed, and a shelter to sleep at night. You can kill mobs, pick rocks, and mine stones.
As you get more and more advanced, you'll move on to stone tools, then iron tools, and eventually diamond tools. If you've played the game, you know that reaching the diamond level requires deep adventures down scary caves and a lot of time and passion.
But this chapter is all about essentials—the wooden and stone tools of the privacy world. These are the bare minimums and basics that form the building blocks of your digital privacy and security. The essentials in the privacy world are different, though: they include encryption tools, anonymity tools, VPNs, emails, secure messengers, password managers, and multi-factor authentication tools. These things are the bare minimums for privacy and match most people's threat models.
Passwords and Password Managers
Passwords are what protect our accounts, devices, and secrets. We need to take all actions to keep them safe, secure, and accessible only to ourselves. Trying to remember a hard password is a bad idea, and I've already explained why. If you use a single password for everything, no matter its complexity, if a data breach containing your account happens, then all your other accounts are accessible using that leaked password. And if you try remembering different passwords for every website, you will likely forget them all. Humans aren't that good at memorizing random passwords, especially if you don't recall them often.
Here, password managers come into play. Password managers are software, either online or offline, designed to store passwords and other notes and secrets safely and securely using encryption. The content inside them is accessible through one password, usually known as the master password. When using a password manager, you memorize a complex password as your master password, which is used to access other passwords inside your password manager's vault. Now you don't need to remember any other passwords or secrets.
A good password manager should have these characteristics:
- Encryption: It needs to be encrypted. Never use a password manager if you're unsure of its encryption.
- Open Source: They should be open-source. While open-source software isn't necessarily safer, being open-source allows us to check their code and the implementation of encryption to ensure they are safe.
- Independent Audits: They must be audited independently. We aren't cryptography analysis experts, so an audit will reveal if there are any flaws in the cryptographic implementation of the software's encryption.
- Offline or Self-Hosted: They should preferably be offline or self-hosted. There is no problem with a cloud-based password manager if it is implemented correctly. Even if their database gets leaked, the passwords should still be encrypted and secure. However, using a self-hosted or offline password manager, like Bitwarden (which can be self-hosted) or KeePass, minimizes the risk of leakage because it is far less likely that you will be targeted more than a password manager's server with thousands of users.
Choosing a Secure Master Password
But how can you generate a secure master password? You need to forget the idea of passwords being random strings of letters, numbers, and punctuation characters. They become really hard for humans to memorize but not as hard for computers to crack through brute-force attacks. On the other hand, passphrases—lists of words separated by a character—are easy for humans to remember but much harder for computers to crack because they are usually longer and have more entropy than a typical password. They are easier to remember because they are words, and words have meanings to us, though not to computers. To computers, they still appear as random strings.
These passphrases are called Diceware Passphrases. An example of a Diceware passphrase is: Batboy Wielder Defective Squire Facial Reptilian Monologue Avatar
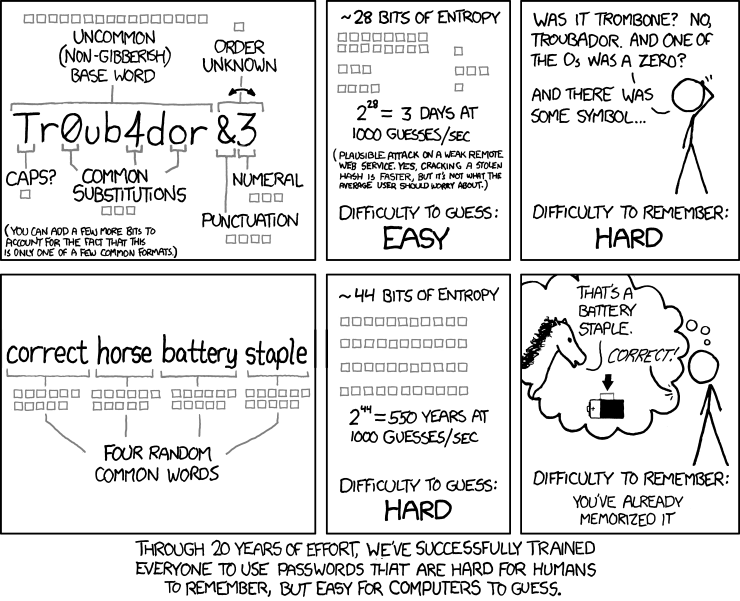
Avoid changing your master passwords too often unless you suspect that it has been compromised, to minimize the risk of forgetting it. Also, a good practice would be to have an encrypted backup of your passwords stored somewhere safe, ideally outside your devices and with a different password (in case you forget the main password), so you can restore your passwords and minimize the risk of losing access to your accounts.
Email Security
Email services aren't secure by nature; new technology usually comes before security, and that's true for email as well as for the earliest protocols of the internet. But this lack of security can be overcome to some extent by adding layers of encryption to email services.
The first layer of encryption needs to be added to the communication channel. By "communication channel," I mean the channel that the data goes through to get to its destination, not the email content itself. This can be done by adding TLS to the transport layer of the email protocol. Nowadays, most email service providers have TLS enabled by default, but if you self-host your email service, you'll need to ensure transport layer encryption is enabled.
The second layer of encryption would be for the email content. This can be achieved using PGP or S/MIME encryption, but you will need to have your recipient's public key to send them encrypted emails. There are encrypted and privacy-focused email providers like ProtonMail and Tutanota that can eliminate this need for having the public key, provided that both sender and recipient use the same email provider. For example, two ProtonMail users can send each other encrypted emails without having to know each other's public keys.
Even if you encrypt the content of the email, the metadata would still be unencrypted. This metadata can include:
- Sender Email Address: The email address of the person sending the email.
- Recipient Email Address(es): The email address(es) of the recipient(s) of the email.
- Timestamps: The date and time when the email was sent and sometimes when it was received.
- Subject Line: The subject line of the email, which summarizes its content.
- Message-ID: A unique identifier for the email message.
- Return-Path: The email address to which bounced emails are returned.
- Received: Information about the email servers and networks through which the email passed during transmission.
- X-Mailer: An optional field indicating the email client or software used to compose the email.
- MIME-Version: The version of the Multipurpose Internet Mail Extensions (MIME) protocol used in the email.
- Content-Type: The type and format of the message content, such as text/plain for plain text or text/html for HTML-formatted content.
Messaging Security
Most chat messages aren't secure either. For instance, Telegram, a messaging app that claims to be encrypted and secure, doesn’t even have end-to-end encryption (E2EE) enabled by default. Even when it does offer E2EE, it is only available on mobile clients, meaning you cannot use Telegram securely with the desktop client. Worse, Telegram breaks the first and most important rule of cryptography, which states, "Do not roll your own crypto," by using a self-rolled cryptographic scheme for its E2E encrypted chats. Additionally, Telegram's servers are all closed source; nobody knows how the messages and data on Telegram are stored, whether they are encrypted, or who has access to these servers. Telegram is a perfect example of a poor messaging app in my opinion. While there are messaging apps that are worse than Telegram, they do not claim to be private and secure. Therefore, I will use Telegram as a bad example to explain what a messaging app should have.
- End-to-End Encryption: A secure messaging app should offer E2EE with a known and audited cryptographic scheme and implementation. Telegram provides E2EE to some extent, but its cryptography is questionable.
- Anonymous Sign-Up: A private messaging app should allow you to sign up anonymously, typically using an email. Telegram and Signal use phone numbers, which is reasonable for reducing spam, but there are ways around it, such as buying an anonymous VoIP number using Monero or cash.
- Transparency: A secure messaging app should be transparent about how they store data, what data they store, and under what circumstances the data can be handed over to authorities.
- Metadata Collection: Every message and account has some metadata that isn't usually encrypted. Telegram collects a lot of metadata about you, including your name, sign-up date, IP addresses, 2FA email, phone number, contacts, people you frequently talk to, and all your messages (if you do not use E2EE). They can hand this data over to authorities if required. In contrast, Signal collects little to no metadata about you and doesn’t have much to hand over even if a court order compels them to do so.
- Popularity: We can't make everyone use the same app. If everyone I know uses Telegram, I have to use Telegram too. This is a significant factor for a messaging app. I might use Matrix over Signal, despite Signal having better security and collecting less metadata than Matrix, because most people I talk with use Matrix, so I have to make some sacrifices.
Your threat model plays a huge role here. You might not care if your messages with friends are readable by Telegram or any other company. It depends on you and your threat model.
Choosing a secure VPN
Normally, when you use the internet, your ISP can technically see all the data passing through the network. However, with most websites and services supporting TLS/SSL encryption today, your ISP cannot see much of the data, but they can still determine the IP address and domain name that you're requesting. Anything that your ISP can see, your VPN provider can see as well. Because of this, VPNs are mostly a shift in trust. For example, my ISP logs a lot of information that I prefer not to be logged and retains this data for a long period of time. However, the VPN provider I use (ProtonVPN and Mullvad) promises not to log anything. They are reputable, privacy-focused VPN providers that allow anonymous payments, especially Mullvad VPN. In this scenario, I prefer using the VPN all the time because I trust it more than my ISP. Sometimes, using a VPN is about bypassing censorship. VPNs are great for this as they encrypt the data passing through the network, making it difficult for censorship systems to detect. But even in this case, it is still a matter of shifting trust, and the VPN should collect little to no data about us and our activities.
graph TD;
Client[Client Device]
ISP[Internet Service Provider]
VPN_Server[VPN Server]
Destination[Destination Server]
Client -->|Encrypted VPN Tunnel| VPN_Server
VPN_Server -->|Regular Traffic| Destination
Client -->|Regular Traffic| ISP
ISP -->|Encrypted VPN Tunnel| VPN_Server
ISP -.->|Encrypted Data| Destination
For me, a VPN provider should have the following characteristics:
- Strong Encryption: It should use secure encryption methods and protocols, such as WireGuard and OpenVPN, and an encryption method that supports perfect forward secrecy. Perfect forward secrecy ensures that encrypted data cannot be accessed even if the actual key is compromised.
- No-Logs Policy: A private VPN provider should not keep logs of user activities, connections, timestamps, or IP addresses. For example, VPN providers like Mullvad, ProtonVPN, and Windscribe do not collect much about your traffic.
- DNS Leak Protection: A secure and private VPN should ensure that DNS queries are routed through the VPN tunnel, not through the user's ISP. This prevents the leaking of visited websites to the ISP.
- Kill Switch: A private VPN should provide a feature that disconnects the user from the internet if the VPN connection drops, ensuring that no data is transmitted over an unencrypted connection.
- IP Address Masking: The VPN should hide the user's real IP with one provided by the VPN servers.
- Multi-Hop: A useful feature for a VPN to have is multi-hopping, which routes user traffic through multiple servers in different locations, adding an extra layer of security and privacy.
- Secure Authentication: An ideal VPN provider would have multi-factor authentication systems (like TOTP or even SMS/email authentication codes) to protect user accounts.
- Private Servers: It should use private or dedicated servers rather than shared ones to reduce the risk of data interception.
- Obfuscation: It should provide obfuscation features to bypass censorship systems like Deep Packet Inspection (DPI), making the VPN traffic appear like regular traffic, usually using an obfuscation protocol like obfs4 or ScrambleSuit.
- Jurisdiction: It is better to be based in a country with strong privacy laws and outside the influence of surveillance alliances like the Five Eyes, Nine Eyes, or Fourteen Eyes.
- Regular Audits: It should have regular security audits by independent third parties to verify the no-logs policy and the overall security of the service.
These characteristics can vary based on the user's threat model. Not everyone cares about multi-hops and no-logs policies. You should always act based on your threat model.
Operating Systems Security/Privacy
Operating systems are software that communicate with the hardware and manage hardware resources, such as memory allocation, task scheduling, I/O processes, and more. While these are core functionalities of an operating system (or its kernel), layers of software stack up on the kernel to create a usable operating system, which can greatly impact the privacy and security of its users.
The main operating systems I will discuss are iOS, Android, Linux, Windows, and macOS:
Android
The Android Open Source Project (AOSP) is a decent and secure operating system, featuring verified boots, app sandboxing (a crucial security feature), and a robust permission management system.
However, when you buy an Android phone, the operating system on it is usually not vanilla Android. It is often modified with many additional apps and features primarily used for gathering data from user activities.
There are custom ROMs designed to address this issue. Even without custom ROMs, many unnecessary features can be disabled to minimize data collection.
More important than data collection is ensuring the phone is updated with the latest security patches if available, and avoiding rooting (as it can break app sandboxing and compromise the phone's security).
On some phones, like Google Pixels, you can install GrapheneOS, a very secure and privacy-respecting Android custom ROM.
iOS
Unlike Android, iOS is not open source, so we cannot be sure how it operates internally, and there is not much you can do to change it if you have an iPhone. However, you can tweak the settings and disable unnecessary features to harden it for your needs.
Windows
Microsoft Windows is one of the most common PC operating systems, but its security and privacy are not admirable. It sends a lot of telemetry data to Microsoft, it is closed source, making it harder to find and fix security bugs, so many zero-day vulnerabilities exist for Windows.
There might be settings to tweak and adjust, but the safer option would be to install a Linux distribution and use Windows in an isolated virtual machine if you absolutely need to have a Windows machine.
Linux
Linux is a free and open-source operating system with excellent privacy features. Because it is open source and has been around for a long time, very few zero-day vulnerabilities exist for it.
Linux has thousands of distributions to choose from, making it suitable for any needs you might have. There are also many variations of the Linux kernel itself, such as linux-hardened, which is designed to have more security features enabled by default.
These were the bare minimums of privacy and security. As the book progresses, the chapters will become more technically advanced and more focused on anonymity. The next chapter will be all about encryption, as it is the building block of security in the online world.
Chapter 5
Encryption tools are a non-separable part of security, privacy, and anonymity online. You can't achieve anonymity if you don't have privacy, you can't have privacy if you are not secure, and you can't be secure if there's no encryption.
Encryption is like the house you build in Minecraft; it only allows you inside, not the zombies and the mobs, and keeps your stuff safe when you're not home. The encryption algorithm and scheme would be the material that your house is built with. A weak encryption scheme/algorithm is like a Minecraft house built with dirt or wood; it can be destroyed by a creeper blowing up near it or catch on fire if you accidentally light a flint on it. The more proven and tested the algorithm is, the more secure it becomes. So, the first rule of encryption is to never roll your own encryption, as that can be like building a Minecraft house out of thin air, with no structure and no good quality material, and it will fall apart with the most effortless attacks of a professional.
Don't Roll Your Own Cryptography
If you're new to the cryptography world, you might think if a cryptographic algorithm is not known to others it will be more secure, but this is not true in any way. A cryptographic algorithm should be secure not because no one knows how the algorithm works but rather due to the security of the algorithm itself. It should go through all sorts of attacks, both the algorithm and the implementation of the algorithm. When it comes back untouched, then it is considered safe to use. For example, algorithms like AES, Twofish, Serpent, and ChaCha20 have all gone through the process of testing by actual mathematicians and cryptographers and have been around long enough for their security to be proven.
When you decide to create your own cryptographic scheme or algorithm, it's like witchcraft compared to a well-known cryptographic algorithm because you're not a mathematician, cryptographer, or cryptography analyst. You can't build your own algorithm nor test and attack your algorithm effectively. When your algorithm faces a real professional who has been working with this type of stuff for decades, your algorithm doesn't stand a chance.
Here is a quote from the book, Introduction to Cryptography, by the creator of PGP:
When I was in college in the early 70s, I devised what I believed was a brilliant encryption scheme. A simple pseudorandom number stream was added to the plaintext stream to create ciphertext. This would seemingly thwart any frequency analysis of the ciphertext, and would be uncrackable even to the most resourceful government intelligence agencies. I felt so smug about my achievement.
Years later, I discovered this same scheme in several introductory cryptography texts and tutorial papers. How nice. Other cryptographers had thought of the same scheme. Unfortunately, the scheme was presented as a simple homework assignment on how to use elementary cryptanalytic techniques to trivially crack it. So much for my brilliant scheme.
From this humbling experience, I learned how easy it is to fall into a false sense of security when devising an encryption algorithm. Most people don’t realize how fiendishly difficult it is to devise an encryption algorithm that can withstand a prolonged and determined attack by a resourceful opponent.
-- Creator of PGP, Phil Zimmermann
Even the Most Secure Algorithms Can Be Vulnerable
It is not only the cryptographic algorithm that has to be secure; the implementation of it needs to be secure, well-known, and audited as well, both for hardware and software level implementations. Several attacks can be done through the implementation of an algorithm, for example:
- Timing Attacks: An attacker measures the time it takes to perform cryptographic operations and uses this information to deduce secret keys.
- Simple Power Analysis (SPA): An attacker analyzes power consumption traces to extract keys or other sensitive information.
- Differential Power Analysis (DPA): An attacker collects power consumption data over many encryption operations and uses statistical methods to deduce the secret key.
- Electromagnetic (EM) Attacks: An attacker uses EM emissions to gain information about the internal state of the device and extract secret keys.
- Fault Injection Attacks: An attacker uses techniques like voltage glitching, clock glitching, or laser fault injection to induce faults and analyze the erroneous outputs to deduce the secret key.
- Cache Attacks: An attacker uses cache timing information to infer which memory accesses are made during cryptographic operations and deduces secret keys.
- Cold Boot Attacks: An attacker freezes the RAM to preserve its state and then reads the memory contents after rebooting the system to extract encryption keys.
- Differential Fault Analysis (DFA): An attacker compares faulty and correct outputs to deduce information about the internal state and secret keys.
- Glitching Attacks: An attacker uses power or clock glitches to cause incorrect operations in cryptographic algorithms, then analyzes the faulty outputs to extract keys.
- Buffer Overflow: An attacker crafts input data that causes buffer overflows and gains control over the execution flow to extract keys or sensitive data.
- Side-Channel via Shared Resources: An attacker running code on the same machine as the cryptographic software can use shared resource behavior to infer secret keys.
- Physical Attacks: An attacker uses techniques like microprobing to directly read out memory contents or manipulate hardware components.
These attacks can be done on algorithms that are considered unbreakable, only through the implementation side of things. All these attacks can be prevented as well. A well-known software or device that has been audited is probably secure against all or most of these attacks.
Some best practices would be keeping the software updated, looking for independent audits, using proven libraries (if you are developing a tool that needs encryption), and using standard encryption algorithms, modes, and schemes.
Encrypt Your Data at Rest
Encryption doesn't always have to be for communication channels, messengers, VPNs, etc. Your offline data needs encryption too. Just like when you put your important stuff in a safe box and it is available to you only when the safe box is opened, your data on your phone, computer, NAS, USB sticks should be encrypted as well, so only when they are opened is their data available. At rest, encryption doesn't mean that if malware finds its way to your computer it cannot access your data; it means when you don't use it, when it's locked, it is not accessible.
Imagine someone robs your laptop. If it's not encrypted, they can simply take out the hard drive and steal all the data on it, but if it's encrypted and locked, there should be no way to access any of your data.
For the encryption of your hard drives, you can use software like VeraCrypt if cross-platform compatibility matters to you. On Windows, there's BitLocker, and on Linux, you can use cryptsetup or a file system that allows encryption.
But there are differences between container encryption tools like VeraCrypt and cryptsetup and file system-level encryption like fscrypt. Here are some of the key differences:
| Feature | File System Encryption | Container Encryption |
|---|---|---|
| Encryption Scope | Individual files/directories | Entire volumes/containers |
| Integration | Built into file system (e.g., ext4, F2FS) | Separate from file system |
| Performance | Lower overhead, selective encryption | Higher overhead, encrypts all data |
| Key Management | User-specific keys, multiple keys per file/dir | Single key or passphrase per container |
| Ease of Use | Transparent after setup | Requires mounting/unmounting containers |
| Cross-Platform | Limited to supporting file systems | Broad support (Windows, Linux, macOS) |
| Security | Encrypts data, but not always metadata | Encrypts all data and metadata |
| Use Cases | Selective encryption, performance-sensitive | Full volume encryption, cross-platform needs |
When it comes to full disk encryption, having modern hardware really helps with the security and performance of encryption, as modern CPUs have built-in AES accelerating features allowing them to encrypt and decrypt AES without affecting the I/O performance as much. Also, most modern devices have TPMs (Trusted Platform Modules) which are hardware microcontrollers designed to enhance security at the hardware level by providing a secure environment for generating, storing, and managing cryptographic keys.
Keep Your Backups Off-Site and Encrypted
The most important thing about taking backups of your data is that they need to be stored off-site. Otherwise, you just made a copy of your data; it is not a backup. A good backup can be restored even if your whole house gets burnt down, and it should be restored only by you, not anyone else.
You need to always store your backups securely encrypted, especially for things like crypto wallets, backups of GPG keys, and passwords. This should be done strategically and routinely. For data that is really important to restore, like crypto wallets and GPG keys, you might need to store them in several places, including outside your house (it can be a cloud service as well, just in case of physical disasters), and on different devices like DVDs, USB sticks, hard drives, and SD cards.
For that, you should first develop a backup strategy to know what data is most important, how you are going to perform backups, how you are going to encrypt the backups, and where you are going to store them. Do this on a regular basis if the data tends to change. Some data might not need to be backed up weekly, but some do, and some might change daily. It depends on your data and your backup strategy.
A good and well-known backup strategy is the 3-2-1 rule, which means:
- Three copies of your data: one primary and two backups.
- Two different media types: such as internal/external hard drives, SSDs, and cloud storage.
- One copy off-site: store a backup in a remote location or in the cloud to protect against physical disasters.
For cloud storage, it is better to use a reputable cloud storage provider. Even something like Google Drive, though its privacy is not good, will be a more reliable option compared to other services. You can also host your own cloud storage, but it will never be as reliable as a huge company like Google.
You can also invest in a NAS for automatic and centralized backups, and you can configure it for RAID (Redundant Array of Independent Disks) for data redundancy and protection. Be sure to take snapshots and version your backups to be able to restore them easily.
Always regularly test your backups to make sure they're valid and restorable. Otherwise, you might be backing up corrupted data for years, and when you need to restore your data, you can't; all your data is gone.
Lastly, develop a disaster recovery plan and ensure you have clear procedures for data restoration in case of data loss incidents.
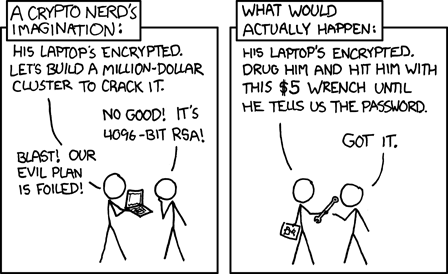
Five Dollar Wrench Attack
No matter how securely a hard drive is encrypted, it is always vulnerable to the 5-dollar wrench attack, meaning someone can always beat you up with a 5-dollar wrench to make you give up your passwords. How can this be prevented? Well, it is complicated, but there are some things you can do.
1. Have a Kill Switch
Creating a kill switch system in which, if a specific password is entered, the key file is permanently wiped could save your data by making it inaccessible forever for everyone, including yourself. Now even you can't restore your data.
Or you can create a panic button instead. In case of something like kidnapping, it would alert the authorities. It all boils down to your own unique threat model. Based on the threats that might target your data, you might need to change this to suit the situation.
2. Have a Decoy System
You can create fake wallets and fake accounts and reveal those instead of the real ones. For example, some activists have created a version of Telegram called Partisan Telegram to help Belarus protesters. The way it works is you can set a lock on your Telegram and have multiple PIN codes on it and program each PIN code to do certain things. For example, if you enter the PIN "1234," it will wipe all data and send a message to everyone to alert them, but if you enter "1349," it will show a decoy account, and if you enter "6782," it will function normally.
These decoy systems can really help with situations like a protest where you might get arrested or have your devices searched. Combining them with kill switches can both fool the attacker and, at the same time, delete all the data.
3. Reduce the Value of the Target
Store minimal sensitive data on the devices that are most vulnerable to this kind of physical attack. For example, you don't need so much sensitive data on the phone you take out with you. Frequently back up sensitive data securely to a secure location. It can be a physical location or a remote cloud, so the data is not all in one place and not always with you.
4. Use Multi-Factor Authentication for Sensitive Data
Use physical authentication devices like YubiKey that require both possession of the token and a PIN or password, and keep them in a safe place. This way, your data is not accessible without the authentication device. You can hand them the passwords, but they still won't be able to get inside.
Avoid biometric authentication; it is not resistant to physical force. Someone can forcefully use your fingerprint if they need to.
5. Be Aware of Social Engineering Tactics
Some might use social engineering tactics instead of force, especially if they are in a position of authority. Always be aware of the tactics and mind games someone might play to get you to hand them sensitive information, passwords, and credentials.
Understand your legal rights regarding self-defense and data protection in your jurisdiction. Have a list of emergency contacts, including legal counsel, who can provide immediate assistance in case of coercion or threats.
These were all I had on encrypting and securely storing sensitive information. The next chapter will be about footprints and fingerprints and what actions can be taken to minimize or even erase the trace you left behind when you didn't care much about privacy.
Chapter 6
Everything you touch leaves your fingerprint on it, and everywhere you go, you leave your footprints behind, making you identifiable and your actions traceable back to you. Unless you're wearing gloves, are cautious of not leaving your DNA behind, and wipe your footprints as you go forward, the same goes for you when you use the internet.
On the internet, we all have unique fingerprints and leave footprints behind as we use it. The more you use it, the more unique your fingerprints become and the clearer your footprints become.
This chapter is all about making yourself as less unique as possible and covering your footprints as much as possible. It might be impossible to fully wipe your old footprints because anything you put out there on the internet can stay there forever, and it's impossible to not have a fingerprint at all. The key is to create multiple unique fingerprints and keep them separated from each other. This strategy will save you a lot of energy, time, and anxiety, and make it sustainable for the long run.
Separating Fingerprints
We all have real identities in the real world, and we have to use the internet with our real identity too. We can't stop using credit cards and banks and buy everything on Tor using Monero. That is simply not possible. But we can separate our real identity fully, giving it its unique fingerprint, unique behavior, and unique writing style, and for our other identities, we can separate them as well.
For example, an activist who wants to remain anonymous can still have two unique fingerprints: one for their real identity and one for their activist identity. The uniqueness of the fingerprint is never the problem in such scenarios as long as you keep these fingerprints separated. If you use your activist fingerprint to do your real-world stuff, then it's a problem. Now you've cross-contaminated the identities. But if you don't, it won't be a problem. Even if they start tracking your activist identity, it won't lead them to your real identity. It has its own footprint, which traces nowhere near your real identity, and it has its own unique behavior, unique writing style, etc.
However, sometimes you truly need to look like others, such as when someone buys stolen data off the dark web (not that I encourage illegal activities as such). Then it will be best to look like everyone else on that website. Again, it all depends on your threat model.
How can you separate your fingerprints? Here are some tips, but you should take a look at your threat model and build a strategy based on that.
- Create separate working environments: It can be having multiple different accounts on your computer, phone, etc., or having fully separated virtual machines set up for each different identity.
- Create separate accounts: Have different emails, cloud storages, VPN accounts, etc., for each identity.
- Create separate backstories: Have different identities, and give them separate lives and backstories. This will make it easier to keep up with them.
- Create separate behavior patterns: Your typing style (speed, accuracy, etc.), writing style, expressions and words you use, the way you respond, your clicking and mouse movement patterns, the websites you usually visit—these are all behavior patterns that can cross-contaminate identities.
- Use fingerprint-resistant tools: Use tools like Tor Browser, a hardened Firefox, Whonix OS, etc.
There are analysis algorithms to match these unique behaviors to other users and accurately pinpoint the user who has the same behaviors and fingerprint. Even if such algorithms are not used by authorities, they exist, and they can be used. So they might and will be used, just like how they're used nowadays for marketing and advertisement purposes. Most of the time, privacy is about preventing such things from happening.
Erasing Your Old Footprints
Although it is hard, it is not fully impossible. You can still remove some of your footprints that you left behind years before. First, you need to see what identity you want to wipe out. Then start creating a full list of everywhere you have signed up, posted something, or bought something. An easy way to gather this data would be going through your emails—all of them—and seeing what websites have sent you emails for logins and sign-ups. List them all.
Then you can go to each website. If they allow you to delete your account, delete it. For cases like Twitter and other social media, the best approach would be to first delete everything—comments, posts, profile pictures, bio, location, etc.—and wait for a few weeks. Then delete the account. This will allow the crawlers and search engines to update their information on the account, so your old posts won't show up in search results after you delete your account.
For some websites and services that don't allow you to delete your account, first change all your information on them, then email them to delete your data. In most cases, they will. For the data that you didn't put out there, you can send a DMCA notice and ask them to take down your data. You can do this to take down your data off the search engines as well.
There are some services that can automatically delete you off the internet as well. After you manually delete everything, you can use services like "DeleteMe" to delete everything else. They can also delete and notify you if future information is out on you.
After deleting everything, try to forget it. Do not play around with it anymore if you want the identity to be erased from the internet. Live your life and let it die, hopefully. Also, take notes for the next identity so you won't need to do this again. Make sure you always provide little to no sensitive and unnecessary information when you create and use accounts, and be very minimalist about creating accounts. Only create one if you absolutely need to. Most of the time, you don't. Or if you want to try it out, create a quick one-time identity to test things out.
Your Digital Identifiers
Like in the real world, where our fingertips are unique identifiers or our other biometric features, in the digital world we have those identifiers too. When these digital identifiers are combined together, they can create a fingerprint more unique than those on our fingertips. And this is not only about your software; each piece of hardware that you use has a unique identifier as well.
The good news is most of these identifiers, both at the hardware level and the software and network level, are spoofable and changeable. It's really easy to change a fingerprint in the digital world; the hard thing, and almost impossible thing, is to not have one.
Hardware Identifiers
Each hardware component manufactured comes with a unique identifier, which has been used for device management, network administration, security, etc. But now they can be used to identify users, just like when police gather fingerprints of someone from a crime scene. They can now get your MAC address and see where else you have been with your laptop.
A MAC address, or Media Access Control address, is a unique identifier set by manufacturers for network interfaces for communications on the physical network segment. It is used for identifying devices on local networks, network access control, and tracking devices. It can be changed quite easily on the software level. For example, my Android 13 Nokia phone allows me to have a random MAC address whenever I connect to a Wi-Fi network that I don’t know. MAC address spoofing is relatively easy, and to be honest, it is not that much of a concern. A MAC address is only used on local networks, not the internet, so tracking it is really hard and pointless. However, it is something to keep in mind if you use a network that is not yours; it is always a good idea to spoof your MAC address.
But there’s an identifier in all of our phones that is not changeable, and in some countries, is tied to your real identity. It can leak your approximate location even if your phone has no SIM card in it, and that’s your IMEI and IMSI. The IMEI (International Mobile Equipment Identity) and the IMSI (International Mobile Subscriber Identity) are unique numbers created by phone manufacturers. Every time your phone connects to a mobile network, it registers with your IMEI and IMSI. Even if there’s no SIM card in your phone, because of emergency calls, you still connect to cell phone towers.
The mobile network can log and store the timing of your connection to each cell phone tower, and based on your signal strength, how far you were from it. This means that, at any given time, the network can determine where your phone has been. Your IMSI, in some countries, is directly tied to your real identity because you need to buy SIM cards with your real ID, which automatically links the phone to your actual identity whenever you use it. Also, the IMEI can be traced back to your real identity if you didn’t buy the phone in an anonymous way. Additionally, operating system companies like Google and Apple keep logs of your IMEI and IMSI identifiers tied to your Google/Apple accounts, so they can trace back and see what other accounts have been tied to this phone before.
It is possible to change your IMEI/IMSI, but in some countries, it might not be legal, and in others, it can break the functionality of your phone because they link your IMSI to your SIM card number, and you won’t receive any services if you change it.
Another identifier is your CPU. Each CPU has a CPUID that can reveal information about details of the CPU to software, such as processor type and what features it implements. Also, almost all modern CPUs, including Intel and AMD, have a hidden management platform such as Intel Management Engine for Intel processors and AMD Platform Security Processor for AMD processors. These management platforms are literally small operating systems running on your CPU and have full access to your computer’s network. They could be accessed to de-anonymize users. For Intel CPUs, there’s no good way to turn its management platform off other than buying an old CPU that doesn’t have this feature, but for some AMD CPUs, it can be turned off in the BIOS.
Also, your Bluetooth devices have identifiers like your network interfaces, but that is less of a concern than the network since Bluetooth addresses are often randomized, and most operating systems randomize those addresses. A good practice is to disable Bluetooth when you don’t need it.
Software Identifiers
Your browser has the most software identifiers, which alone can make you unique, and most of the time they are combined with physical identifiers like the CPU you use or the details of your monitor, etc.
One of these identifiers is the user agent string. The user agent string is sent by the browser to the server and identifies the browser type, version, and operating system. It is quite easy to change by hardening your browser or using Tor Browser.
Also, if JavaScript is allowed on your browser, it can read a lot of data from your browser, such as browser type, time zone and language, fonts installed, operating system and version, screen resolution, and color depth. If JavaScript is enabled, it can also perform canvas fingerprinting, WebGL fingerprinting, and AudioContext fingerprinting.
Canvas fingerprinting is a technique that uses the HTML5 canvas element to draw graphics and capture the unique rendering characteristics of a device. The website uses JavaScript to instruct the browser to draw a hidden image or text on a canvas element. This drawing operation can include various shapes, colors, text fonts, and sizes. Once the drawing operation is complete, the browser extracts the pixel data from the rendered image or text. This data is essentially a long string of numbers representing the color and brightness of each pixel. Different browsers may render graphics slightly differently due to variations in their rendering engines. The same browser may produce different results on different operating systems. Additionally, hardware differences like graphic cards can affect the rendering process, leading to unique variations, and variations in installed fonts and how they are rendered can contribute to uniqueness.
WebGL is used for rendering interactive 3D and 2D graphics within any compatible web browser without the use of plugins, but it can be used to fingerprint users as well. The way it works is that the website uses JavaScript to instruct the browser to render a 3D object or scene using the WebGL API. This rendering involves various aspects such as textures, lighting, shading, and other graphical effects. After rendering, the browser extracts data from the rendered image or scene. This data can include the pixel values, but also more complex information about the rendering process, such as the attributes of the graphics card and drivers. Then, like canvas fingerprinting, the rendering data is hashed using a cryptographic hash function, creating a unique fingerprint. This fingerprint is unique due to the differences in how different devices render the same 3D object.
AudioContext fingerprinting uses the AudioContext API to generate a unique identifier based on the audio processing capabilities of a user's device. It works based on the fact that different devices and environments will process audio signals in slightly different ways due to hardware and software variations. First, the website uses JavaScript to create an instance of the AudioContext object and generate an audio signal, typically using oscillators or other sound sources. Then, the generated audio signal is passed through various audio processing nodes, such as gain nodes, filters, or analyzers. These nodes modify the audio signal in ways that are subtly influenced by the hardware and software environment. After that, the processed audio signal is captured, often by using an AnalyserNode to capture the audio data in the form of frequency or time-domain data. Lastly, the captured audio data is hashed and used as a unique fingerprint.
Also, the Battery Status API, Device Memory and Hardware Concurrency, Installed Fonts, Network Information API, Touch and Pointer Events, Applications and Uses, and user behaviors such as the way they use the mouse and keyboard, etc., can be used to create a unique fingerprint as well.
Browser Hardening or Tor Browser
You don't need to use Tor Browser for activities that are tied to your real identity or that are not meant to be anonymous. But hardening a browser, on the other hand, can help a lot more with your privacy concerns by making each browser profile dedicated to one identity and hardening it based on that identity's needs and your threat models.
The way that Tor Browser works is to make you like everybody else on the Tor network. If you use Tor Browser to check in on your bank account or anything else that is tied to a real identity, then you're even more unique than before. Also, the important thing is that you should not change anything in Tor Browser; any slight changes, like installing a plugin or changing settings, can make you much more unique than you would have been without Tor Browser.
But hardening a browser does give you a unique fingerprint, and that is right. However, it also can provide you more security and privacy if you use it correctly, meaning each browser profile should be set up for one specific task or identity. For example, you can have one hardened Firefox profile for watching YouTube and listening to music on SoundCloud, one for your online identities and anything related to that, and one for your real identity. This way, you can choose what task or identity needs are and set up your browser based on those needs.
For hardening browsers, there are a lot of resources out there, especially for Firefox. For example, for Firefox, there is Arkenfox, which provides you a list of carefully selected options and settings for Firefox to enhance its privacy. Using something like Brave for general usage is good too, as it has pretty decent privacy settings and features by default.
You can have multiple browsers for different needs as well, for example, hardened Firefox profiles for different tasks that require specific setups, Brave for general usage, and Tor Browser for when you need to stay anonymous.
It always boils down to your threat model and your specific needs, so always take actions based on that and save yourself a lot of hassles and mistakes too.
That’s it for this chapter. In the next chapter, we will cover creating an anonymous identity, performing tasks anonymously, and maintaining that anonymity.
Chapter 7
In the early 2000s, a whistleblower known only as "Deep Throat" played a crucial role in exposing the Watergate scandal, which eventually led to the resignation of U.S. President Richard Nixon. Deep Throat was later revealed to be Mark Felt, a top official at the FBI.
Felt chose to remain anonymous because he feared retribution from powerful political figures and potential harm to his career and personal life. By meeting secretly with journalists Bob Woodward and Carl Bernstein, Felt provided critical information that helped uncover illegal activities and abuses of power within the Nixon administration.
His anonymity allowed him to share the truth without facing immediate consequences, ultimately leading to significant political changes and reinforcing the importance of accountability in government. Mark Felt's story shows how anonymity can allow people to bring positive change to the world, rather than doing destruction to society. It's a double-edged sword as well as a slippery slope.
Taking away people's anonymity means silencing dissenting voices and creating an environment of fear in which society halts. When individuals can't speak out without risking their safety, privacy, or lives, we lose dissenting opinions, and the creativity of a society dies out. It will start moving backwards, and fear will slowly become the norm of society, passing from one generation to the next, slowly taking away what makes us different from other animals.
Creating Another Identity
As I mentioned in previous chapters, creating a full identity can really help in managing identities and keeping them as separate as possible. Based on your threat model and what you're going to do, you might need to create a pseudonym for yourself and tie it to your anonymous activities.
There's a difference between pseudonymity and anonymity. Pseudonymity means giving your anonymous identity a name, so people can recognize you and your work, for example, a writer using a pen name. Anonymity means hiding one's identity entirely so that there is no way to trace or identify the individual behind the actions or information.
You can still be anonymous and have a pseudonym. Rather than being nameless, especially if you're an activist, writer, or whistleblower, you might need a pseudonym or a fake identity that people would recognize your work with. People can connect better with someone who has a name and identity, even if it's not real, rather than a nameless user on the internet.
Pseudonymous users can build a reputation and credibility over time, while anonymous users cannot build a reputation tied to a specific identity.
To create your pseudonymous identity, you can choose one of these paths:
- Create a username/nickname only
- Create a full identity
- Create a combination of both
Creating a Username/Nickname Only
This path is easier; you only have to think of a unique and untraceable nickname or username and tie your activities to that. The drawback is that it can make it harder to gain reputation and credibility, and if you work with other people, you might want to have an actual name and origin as well.
A real-life example of a nickname would be the famous "Dread Pirate Roberts," aka "DPR," which was the nickname of Ross Ulbricht, the creator of the "Amazon of Drugs," aka the Silk Road. Ross Ulbricht had no other name than this, just one name, "Dread Pirate Roberts."
What matters when creating a nickname is that you don't choose something that can be linked to your real identity. That is the only and most important thing when it comes to creating nicknames. Make sure it doesn't reflect too much of your real identity's interests, and make sure you have never used it before.
To prevent links between your real identity and your nickname, it's better to use a nickname generator website. Search for one and choose one that sounds the best to you, and check its uniqueness as well. Google it and see if anyone else has it or not.
Creating a Full Identity
This path involves choosing a country, an origin story, birthday, full name, gender, address, email with that name, etc. Basically, you are creating yourself a full character with its own interests, style of writing, name, birthplace, birthday—everything.
The advantage of this path is that it is really easy to keep it separate from your real identity. If you have to sign up somewhere that requires information, you can enter the fake personal information you created before.
Make sure the name doesn't lead back to you and write it down in a safe place to keep it consistent, so you don't have to change anything if you forget it.
Also, there are a lot of websites that can generate random and fake identities and addresses. Just search for one and you'll find a ton of them.
Create a Combination of Both
This path, in my opinion, is the most convenient. You can have both a nickname and a full identity and use them as needed. For example, for your GitHub, you can use your nickname as the username and the fake name as your name.
This can bring you both reputation and credibility and ease of identity management, while allowing you to use either name based on the situation.
Just make sure the nickname and identity don't lead back to your real identity. You can also create some nicknames by combining the name and information of your fake identity as well.
OPSec and Online Behaviours
When it comes to anonymity, your OPSec and online behaviors are the most important factors. I have covered OPSec in Chapter 3. Your operational security is crucial when it comes to privacy and especially anonymity. Having poor OPSEC and not being cautious about what information you share online is like snitching on yourself.
Other than your OPSEC, your online behaviors play a huge role in maintaining anonymity. These behaviors can be hard to keep consistent. Inconsistent behaviors can create identifiable patterns that can be used to de-anonymize you. Here are some key points to consider:
Typing Patterns (Keystroke Dynamics)
Your typing speed, rhythm, and the way you switch between keys can create a unique fingerprint. Using typing randomizers or maintaining a consistent typing speed can help avoid recognizable patterns.
Mouse Movement and Click Patterns
The way you move your mouse and the speed at which you click can be tracked. Use tools to anonymize mouse movements or standardize your movement patterns to reduce the risk of identification.
Touchscreen Gestures
On mobile devices, swipe and tap patterns can be unique to you. Similar to mouse movements, try to use standardized gestures and avoid developing identifiable patterns.
Browser Fingerprinting
Details like installed fonts, plugins, screen resolution, and color depth can create a unique browser fingerprint. Use browsers or extensions that randomize or block these details, such as the Tor Browser or CanvasBlocker.
IP Address and Network
A static IP address is more easily trackable. Regularly change your VPN or proxy server location to avoid creating patterns. Use public or shared networks along with an anonymizing network like the TOR network for activities requiring high anonymity.
Device Fingerprinting
Information about your device’s hardware, such as the GPU and CPU, can be collected. Use virtualization or disposable devices for highly sensitive activities to avoid leaving identifiable traces.
Behavioral Biometrics
Keystroke dynamics and other behavioral biometrics can uniquely identify you. Consider using virtual keyboards or scripts to automate some typing tasks.
Account and Profile Creation
Using the same pseudonym across platforms can create linkable patterns. Use different pseudonyms and email addresses for different accounts to avoid connections if possible.
Usage Patterns
The times at which you are active online and the frequency of your logins or visits can create patterns. Vary your online activity times and frequency to avoid detection.
Language and Writing Style
Your vocabulary, syntax, and repeated use of specific phrases can be distinctive. Use different writing styles or tools like paraphrasers to vary your text and reduce traceability.
Geolocation
GPS data, Wi-Fi, and Bluetooth signals can reveal your location. Disable GPS, Wi-Fi, and Bluetooth when not needed, or use location spoofing tools to mask your whereabouts.
Software and Version Information
The combination of your operating system and browser version can be unique. Use commonly used software versions and keep them updated to blend in with the crowd.
Social Media and Online Presence
The type of content you post, your engagement patterns, and your network connections can all be used to trace your identity. Limit social media use, employ pseudonyms, and avoid linking accounts to maintain anonymity.
Consistency in these practices is key to avoiding de-anonymization and maintaining the highest level of security.
You might not need to worry about all of these behaviors; see which ones seem more important to your activity. For example, if you're a writer or whistleblower, your writing style can matter a lot more than other things.
Creating an Environment for Your Activities
Every identity needs an environment for their work and activities, and the setup of that environment is heavily dependent on your threat model. Not every identity and activity requires maximum caution and privacy, but some might, based on what you want to do.
You need to tailor this setup to your own situation, but I will show some examples of different environments based on the sensitivity of activities. These may not necessarily suit your specific situation.
Low-Sensitivity Activities
For activities that do not require high levels of anonymity, such as casual browsing or social media use under a pseudonym, a basic setup may be enough:
- Browser: Use a privacy-focused browser like Firefox with privacy extensions such as uBlock Origin, and apply some hardening using Arkenfox, to make it both usable and private. Also, use different hardened profiles for different pseudonyms and activities.
- VPN: A reputable VPN service to mask your IP address and encrypt your traffic.
- Email: Use a privacy-respecting email service like ProtonMail or Tutanota.
- Search Engine: Use DuckDuckGo or Startpage to avoid tracking by mainstream search engines.
- Privacy-Friendly Front-Ends: There are privacy-friendly front-ends for YouTube, Twitter, Instagram, etc., that allow you to browse these websites without having an account on them or sharing too much data.
Medium-Sensitivity Activities
For activities that require moderate anonymity, such as maintaining a blog or participating in forums on sensitive topics, a more cautious setup is necessary:
- Browser: Use the Tor Browser for anonymity and protection against tracking.
- VPN: Combine a VPN with the Tor network for added security. This can impact your network bandwidth, so if bandwidth is a concern, Tor with obfuscation might be sufficient.
- Email: Use secure email services and consider disposable email addresses for one-time communications.
- Device: Consider using a dedicated device or a virtual machine for these activities to avoid cross-contamination with your primary activities.
- Communication: Use encrypted messaging apps like Signal or Matrix (although not as secure as Signal, it allows sign-up with email and you can host your own home server, so it might be better for privacy and anonymity) for secure communication.
High-Sensitivity Activities
For activities that require the highest level of anonymity, such as whistleblowing, investigative journalism, or activism in a dictatorship regime, a maximum security environment is needed:
- Operating System: Use a live operating system like Tails, which can be run from a USB stick and leaves no trace after use, or set up an encrypted virtual machine with Whonix OS.
- Browser: Strictly use the Tor Browser and follow Tor usage best practices.
- VPN: Use a multi-hop VPN service and route your traffic through the Tor network for layered security.
- Email and Communication: Use encrypted email services, PGP encryption for emails, and secure messaging apps like Signal or Wire. Consider using anonymous email services for additional protection.
- Device: Use a dedicated, secure device that is only used for these high-sensitivity activities. Regularly wipe and reformat the device to remove any potential traces.
- File Sharing: Use encrypted file-sharing services and tools like OnionShare to share files anonymously.
- Metadata Removal: Always strip metadata from files and photos before sharing them.
- Geolocation: Disable GPS, Wi-Fi, and Bluetooth on your device. Use location spoofing tools to mask your actual location.
- Operational Security: Maintain strict OpSec practices, such as never using your real identity, avoiding linking different online identities, and being cautious about the information you share.
Anonymizing Tools
To stay anonymous online, you will need to use different tools based on your needs and situations. Not every tool will necessarily improve your anonymity if used without need. Here are some key anonymizing tools categorized by their function and use case:
1. Browsers
-
Tor Browser
- Use Case: High-level anonymity needs, such as accessing the dark web or conducting sensitive research.
- Features: Routes your internet traffic through the Tor network, masking your IP address and encrypting your traffic multiple times.
-
Brave Browser
- Use Case: General privacy-focused browsing for everyday use.
- Features: Built-in ad blocker, tracker blocker, and the ability to use Tor for private tabs.
-
Hardened Firefox Browser
- Use Case: Highly customizable and can be great if fingerprinting is not your main concern.
- Features: Can be set up based on your needs and can provide great anti-tracking features if hardened correctly.
2. VPN (Virtual Private Network)
-
Reputable VPN Providers
- Use Case: Masking your IP address and encrypting your internet traffic.
- Features: No-logs policies, multiple server locations, and additional security features like double VPN and kill switches.
-
Self-Hosted VPNs
- Use Case: Great for bypassing censorship as you can run protocols that have greater obfuscation and are less likely to be blocked by firewalls.
- Features: Can help bypass censorship; no one else can control and access the data passing through the VPN other than you.
3. Email Services
-
ProtonMail
- Use Case: Secure, encrypted email communication.
- Features: End-to-end encryption, based in Switzerland, supports PGP encryption.
-
Tutanota
- Use Case: Privacy-focused email service.
- Features: End-to-end encryption, no tracking, built-in encryption for calendars and contacts.
-
Disposable Email Services (Guerrilla Mail, 10 Minute Mail)
- Use Case: Temporary email addresses for short-term use.
- Features: Provides anonymous, temporary email addresses that self-destruct after a set period.
4. Messaging Apps
-
Signal
- Use Case: Secure messaging for personal or professional use.
- Features: End-to-end encryption, open source, self-destructing messages.
-
Briar
- Use Case: Censorship-resistant encrypted messaging via Bluetooth, Wi-Fi, Tor, with privacy built-in.
- Features: Great for communicating securely in places with no internet or high censorship.
5. Operating Systems
-
Tails
- Use Case: High-security needs, such as whistleblowing or sensitive journalism.
- Features: Live operating system that runs from a USB stick, leaves no trace, routes all traffic through Tor.
-
Qubes OS
- Use Case: Secure, compartmentalized computing.
- Features: Uses virtualization to create isolated environments for different tasks, reducing the risk of compromise.
-
Whonix OS
- Use Case: A security-focused operating system designed to ensure maximum anonymity and privacy. It can also be used along with Qubes OS for additional security and isolation.
- Features: Uses virtualization to create isolated environments for different tasks, reducing the risk of compromise.
6. File Sharing and Storage
-
OnionShare
- Use Case: Securely sharing files anonymously.
- Features: Uses Tor to create a temporary, anonymous file-sharing server.
-
ProtonDrive
- Use Case: Encrypted cloud storage.
- Features: End-to-end encryption, integrated with ProtonMail for secure file sharing.
7. Metadata Removal Tools
- ExifTool
- Use Case: Removing metadata from files before sharing.
- Features: Command-line tool for viewing, editing, and removing metadata from various file types.
8. Search Engines
-
DuckDuckGo
- Use Case: Privacy-focused web searches.
- Features: Does not track search history, anonymizes user information.
-
Startpage
- Use Case: Anonymous web searches using Google results.
- Features: No tracking, IP anonymization, private search queries.
9. Device and Network Security
-
MAC Address Randomization
- Use Case: Preventing tracking of your physical device.
- Features: Changes your device’s MAC address to avoid identification on networks.
-
Public Wi-Fi Caution
- Use Case: Reducing risk when using public Wi-Fi.
- Features: Always use a VPN, avoid accessing sensitive accounts, and consider using a travel router for added security.
10. Behavioral Anonymizing Tools
-
Typing Randomizers and Virtual Keyboards
- Use Case: Preventing identification through keystroke dynamics.
- Features: Randomizes typing patterns or uses on-screen keyboards to avoid tracking.
-
Mouse Movement Anonymizers
- Use Case: Obfuscating mouse movement patterns.
- Features: Tools that standardize or randomize mouse movements.
Not all of these tools are needed, nor are they guaranteed to remain effective over time. The world is constantly changing, so always research and keep yourself updated about privacy and security news and new tools. These companies may also change their policies or effectiveness over time. If you read this book years later, do some research, but the concepts should remain the same, even if the names of the tools have changed.
Purchasing Anonymously
Sometimes, for your activities, you might need to buy things anonymously online, such as a VPS (Virtual Private Server) to host your own VPN or cloud storage, or you might want to buy a VOIP number anonymously to sign up for Signal or Twitter, or pay for your VPN service. In these cases, you cannot pay with PayPal or credit cards or debit cards, as they are easily trackable. Also, you cannot pay with most cryptocurrencies, as they are worse than fiat and PayPal. For PayPal and credit cards, there should be a court order or permit to see who has paid, but for Bitcoin, well, it is a public ledger; everyone can see where the money comes from and where it goes. Everything is transparent. Most popular cryptocurrencies are like that. Your Bitcoin address is not tied to your name directly, that is correct, but you have to buy it from an exchange first or someone sends you some, and the moment you spend your cryptos, it's obvious whose they were. There are some methods like coin mixing, which is not legal in most countries because you're mixing your coins with others' coins.
But there are cryptocurrencies that are meant to be anonymous, like Monero or Zcash (as these two are the most popular privacy coins on the market). Here's how they work:
Monero (XMR):
How it Works:
-
Stealth Addresses: Monero uses stealth addresses to ensure that transactions cannot be linked back to the recipient. A unique one-time address is created for each transaction, which hides the recipient's actual address.
-
Ring Signatures: This cryptographic technique allows a group of users to sign a transaction without revealing which member of the group actually signed it. In a Monero transaction, multiple possible sources of funds are included in the transaction, making it unclear which source is the actual sender.
-
Ring Confidential Transactions (RingCT): This feature hides the amount being transacted. RingCT ensures that the values in a transaction are hidden from everyone except the parties involved, preventing third parties from knowing the amount of money being sent.
-
Kovri Project: Monero plans to integrate the Kovri project, which will route and encrypt transactions through I2P (Invisible Internet Project) nodes, further obscuring the transaction metadata such as IP addresses.
Why It’s Anonymous:
- Obscured Addresses: Stealth addresses ensure that only the sender and recipient know where the funds are going.
- Hidden Transaction Amounts: RingCT hides the amount of every transaction.
- Unlinkable Transactions: Ring signatures make it impossible to determine the actual source of funds.
- Additional Layer of Privacy: The Kovri project adds an extra layer of anonymity by masking transaction origins through I2P.
Zcash (ZEC):
How It Works:
-
Zero-Knowledge Proofs (zk-SNARKs): Zcash uses a form of zero-knowledge proofs called zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge) to enable fully anonymous transactions. These proofs allow one party to prove to another that a statement is true without revealing any information beyond the veracity of the statement itself.
-
Shielded Addresses: Zcash offers two types of addresses: transparent addresses (t-addresses) and shielded addresses (z-addresses). Transactions between shielded addresses are completely private and do not reveal the sender, recipient, or amount being transacted.
-
Selective Disclosure: Users can choose to disclose transaction details to third parties (e.g., for auditing purposes) while keeping the rest of the network unaware.
Why It’s Anonymous:
- Private Transactions: zk-SNARKs allow transactions to be verified without revealing any transaction details.
- Shielded Transactions: Transactions between shielded addresses hide the sender, recipient, and transaction amount.
- Flexibility: Users can opt for transparent transactions when privacy is not needed or use shielded transactions for full anonymity.
- Selective Transparency: Users can disclose transaction details when necessary without compromising overall privacy.
But there are many more privacy coins as well, but if a coin is not well known in the market, most websites probably won't accept it as payments. The acceptance of privacy coins can be limited, and their use for online purchases might be restricted compared to more well-known cryptocurrencies, especially when governments try to regulate these coins or, if they can't, they will try to eliminate them.
Another payment method is cash. Cash money is as private as Monero; I would say Monero is the cash equivalent of cryptocurrencies. Cash transactions do not require personal information, and there is no way to trace them back to you. Also, more importantly, cash is accepted almost everywhere. Some websites like MallwadVPN allow you to send them cash for the VPNs.
Also, you can get prepaid cards with cash for online purchases as well. This won’t link them to your identity if they are bought without providing personal information and they’re paid with cash.
These were some starting points for beginning an anonymous life; it obviously goes way deeper than this. It changes your lifestyle, your communications, everything. The next chapter will be about the skills you need to learn to maintain this anonymity and privacy and to move forward.
Chapter 8
Maintaining privacy, security, and anonymity requires skills, patience, dedication, and a lot of time. This book is supposed to be a starting point for the privacy journey of those people who need it, rather than being a complete guide, as such a thing never existed and never will. Most of the time, you need to do your own research, program stuff the way you need them, configure systems to make them private for you, and there aren't always resources to learn from. You need to learn by trial and error and playing around with different things. The more you expand your knowledge in different areas, the more you can combine them and find new solutions for a problem, and it can be for anything, not just privacy or security.
Your journey will be different than someone else's. What works for you won't work for others; you might need different skills than someone else. What is effective today might not be tomorrow; what is good today might become evil tomorrow. One thing that remains consistent in the privacy journey is the need to adapt because the world never stops changing, and privacy and security are part of it as well. Someday, most of the things in this book might become obsolete, and that is fine if you adapt to the new situation and try to find new strategies and solutions.
Privacy and security aren't destinations you can reach; they're the road and the journey itself. You might not even want to be 100% secure or private, even if it was possible (which it is not and will not be). The best you can do is to find a middle ground between ignorance and chronic fear and paranoia. The more you learn and expand your knowledge, the easier it might be to get there, as you are more aware of threats and know more about ways to protect yourself against them. The key is to remain cautious, persistent, and keep on learning and adapting to the changes.
In this chapter, which is the final chapter, I will go through some of the skills that I find important, but they're not everything. There are a lot more skills, a lot more tools, a lot more techniques that you might find useful. I tried to keep things more general so that most people can use them, but every unique situation needs unique solutions.
Adapt the Hacker's Mindset
Hackers are driven by curiosity; they want to understand how things work, no matter what it is—even if it’s not computer-related. This curiosity involves continuous learning and staying updated with the changes in the world.
Hackers are also good at problem-solving and are creative. They enjoy finding unconventional solutions to problems, and their creativity allows them to see possibilities and connections that others might not notice.
Hackers are persistent and patient, willing to spend hours, days, or even months working on a problem until they solve it.
They pay close attention to details, noticing small elements that others overlook, which allows them to identify vulnerabilities and exploit them effectively.
They constantly test the limits of systems, pushing these limits to discover what’s possible.
Most importantly, hackers are collaborative, working in communities to share knowledge, tools, and techniques. Such communities allow them to build on each other’s work and ideas.
Hackers are aware of the risks involved in their activities and try to manage these risks, balancing potential rewards against possible consequences.
They are flexible thinkers who can adjust their strategies in response to new information or situations.
This hacker mindset helps you understand how systems work, identify potential privacy and security flaws, and explore and test systems to discover new vulnerabilities and ways to protect against them.
Thinking outside the box allows for creative solutions to privacy and security challenges. The ability to adapt strategies and develop new techniques helps protect yourself against new threats.
Paying close attention to detail ensures thorough security checks and correct implementation of privacy measures by noticing small, often overlooked vulnerabilities that could compromise privacy or security.
Persistently testing and evaluating systems helps you find hidden vulnerabilities you didn’t know existed. The continuous improvement that comes with persistent testing will enhance your security and privacy measures over time.
Risk assessment helps you understand potential consequences and implement more effective protections.
Researching Skills
Researching is the biggest part of learning, in my opinion at least. You cannot gather information about a subject if you can't research properly for it. If you are able to research effectively from credible sources, extract relevant information, and synthesize that knowledge to form an understanding, that will not only help with your privacy and security journey but any other field as well.
Using Search Engines Effectively
Search engines like Google not only can help with your research about privacy and security but research about yourself. If you can use them effectively, you can see what information of yours is indexed on them. This can be done by learning advanced search operators, such as site:, inurl:, intitle:, and Boolean operators (AND, OR, NOT) to filter the search results.
And also nowadays most search engines are basically artificial intelligences, so learning prompt engineering can help you a lot as well.
Checking Sources
Checking for the credibility of websites and authors of an article or information and looking for reputable sources which have a good track of accuracy and reliability can save you from gathering wrong and inaccurate information about a subject.
To verify information, one thing you can do is to cross-reference it with multiple sources if possible, this will ensure its consistency and accuracy along multiple sources.
Scholarly Databases
You can also use databases like Google Scholar, JSTOR, and IEEE Xplore to find peer-reviewed articles on privacy and security. And feel free to pirate them if you find it ethical (I find it ethical; knowledge and science shouldn't be behind paywalls, it is what drives societies forward).
Follow Tech News Websites
Follow reputable tech news websites to see what is happening in the world. Also, following some security blogs with reputable authors can help a lot. You can follow the Hacker News (Y Combinator) feed with keywords related to privacy, security, anonymity, and tools like Tor, PGP, etc., to get new articles on them, usually from reputable authors with accurate and in-detail information. Also, you can follow forums and group chats dedicated to privacy and security, for example, Reddit’s r/privacy or the Matrix group chat of Privacy Guides and PrivSec, or Techlore and Surveillance Report on YouTube.
Gather and Organize Information
When you research a subject, try gathering the information at first, then go through it, double-check it and organize it. It will be nice of you if you share it with others, making a positive change by sharing your newly earned knowledge.
Data Management Skills
Having the ability to manage the data and information you share or store is one of the biggest skills required to maintain privacy and anonymity and keep good OPSEC. It includes practices and strategies to protect personal information from getting into the wrong hands, misuse, or breaches. Effective data management is a must in order to maintain data privacy and security. Here are some key skills needed for data management:
-
Data Minimization: Only share, collect, process, and store the minimum data necessary for a specific purpose. Avoid giving unnecessary personal information and opt for services that require minimal data. Share only essential information and avoid oversharing.
-
Encryption: Encrypt data at rest to protect data stored on devices or servers. Encrypt data in transit to protect data as it moves across networks. Use end-to-end encryption to ensure only the communicating users can read the messages.
-
Access Control and Authentication: Use multi-factor authentication systems to prevent unauthorized access to data and use Role-Based Access Control (RBAC) to limit access to data based on user roles (great for separating identities and users on a device).
-
Data Retention Policies: Define how long data should be kept and when it should be deleted. For example, you might want to delete all cookies on your browser every day and your server logs every week. It depends on your needs. Configure systems to delete data after a certain period and periodically review and delete unnecessary data.
-
Metadata Management: Metadata can reveal information about the data itself, like the creation date, author, or location. Always remove metadata from files before sharing them.
-
Backup and Recovery: Ensure backups are encrypted to protect data from unauthorized access. Regularly back up and follow a good backup strategy (explained in Chapter 5).
These are some of the skills and practices for data management. There are a lot more, and you can find more or create your own.
Technical Skills
To obtain and maintain privacy and security requires a lot of technical skills, from programming to understanding networks and operating systems, encryption, and more.
So it should be obvious that you need to learn or level up your technical skills every day. I will point out some starting skills to jump-start your learning journey if you don't know where to start:
Encryption
Encryption is an inseparable part of privacy, security, and anonymity; it’s the chain that connects these three together. Without encryption, there can be no security on the internet. It is really important to know what you're doing when it comes to encryption, as it can go wrong easily due to the complexities of mathematical attacks on encryption algorithms. You don't have to become a cryptographer or cryptography analyst; just having some basic understanding is enough.
You might want to learn about different algorithms, how they operate differently, what attacks can target encrypted information or the encryption process, what algorithms are not safe to use, which implementations of an algorithm are audited and good to use, and what schemes are best suited for your encryption needs. These are things you need to know.
A good starting course on encryption would be the "Introduction to Cryptography by Christof Paar," which can benefit you greatly in terms of a deep understanding of cryptographic algorithms. The course is freely available on YouTube. If it weren't, you could find it by searching elsewhere.
Having a deep understanding of encryption will also help with understanding other tools such as the Tor network, VPNs, multi-factor authentication devices, and more.
Networks
All of your data are passing through computer networks every second. Knowing how these networks work and operate is a must to prevent attacks, leaks, and more. You need to know what is happening when you tunnel your network through VPNs or Tor. You should be able to monitor them for potential leaks, set up firewalls, block unauthorized access to your data, and configure your network for better security and privacy by default.
There are many courses from beginner to advanced on computer networks that you can take. As I said before, feel free to pirate them if you can’t afford them. There should also be plenty of good resources and courses for free on YouTube and other websites. What matters is learning and understanding the subjects. Much of it will come from real-life practice and experience as well.
Programming
To automate tasks like backups, create tools for your specific needs, or read and check source codes of other programs, you need to know some programming. Learning one scripting language like Python or Bash scripting (especially for Linux users) and one system-level language like Rust (which has built-in safety features) would be more than enough.
There are a ton of resources, many of them high-quality and free, for programming that you can use to learn. It will make your journey much easier if you can automate repetitive tasks or build the tools you need that don’t exist. Also, be sure to adopt secure coding practices as you learn.
Operating Systems
Having a deep understanding of your operating system is essential to obtain privacy and security. Especially learning and understanding Linux, as Linux is free and open-source, well-audited, and less likely to have zero-day vulnerabilities compared to Windows. It can be extremely customizable—you can make it operate exactly as you want, not more, not less. This is a great feature when it comes to operating systems. Also, most tools are available for Linux and other Unix-like operating systems.
There are courses like Linux Essentials for Beginners and LPIC1, LPIC2, LPIC3, and Red Hat courses for more advanced users. Make sure to start one of these courses if you decide to install Linux for your operating system, and follow the order from beginner to advanced as it can get confusing.
Virtualization and Containerization
Understanding how virtualization and containerization systems and tools work will help you a lot with isolating different identities, separating tasks, and preventing malicious code from running on your actual system.
There are many resources on these two topics as well. I highly recommend learning about them as they are very useful tools for activity isolation, which is a key part of maintaining good security and privacy, in my opinion.
And the skills don't end here. Anything you learn comes in handy. As I said at the beginning of this chapter, the more skills and knowledge you have, the more you can combine them and create unique and better solutions to a problem.
Communities
We, as humans, are meant to work in communities—together, helping one another and building on top of each other's work. So, it is important to have a community when starting a journey, to ask questions, get help, and give help if you can.
There are a lot of privacy-focused communities, like PrivacyGuides, PrivSec, Techlore, and many more. Being present in these communities will teach you a lot just by reading what others are talking about. I personally learned a lot from the good folks at PrivacyGuides, and it really helped with my own privacy and security journey when I started.
If you're reading this book in English, then you have enough English skills to communicate with others or at least read their messages without problem.
If You Think You Need to Erase Yourself from the Internet
Sometimes paranoia may take over and make you think you need to wipe yourself out of existence, and that is okay and most of the time reasonable.
The first step in this situation is to stay calm and not panic. Panicking leads to irrational thinking and poor judgment.
Delete everything you can from the internet related to the identity you want to wipe out. Dispose of devices you might have dedicated to that identity. If you really want to erase everything, physically destroy hard drives, SSDs, and other storage devices.
Erase and wipe the backups permanently. If you can, find a lawyer and discuss the situation with them.
Live your life again with the hope that nothing goes wrong, because you did all you could.
This is all I had for this book. As I said in the introduction, my hope has been that it can help those good people who are making positive changes in the world and need to start worrying about their privacy and protection. It’s not that nice and pretty a world where every good action is rewarded and appreciated. In some places, doing a nice thing can cost you your life. As disturbing as it is, it is true and should be accepted and fought against. I know this is not a complete book that covers everything, but I think I’ve done the best I could to cover most useful and necessary things. There might be updated revisions of this book in the future that cover more stuff and more important stuff.
Appendix A
VPNs and Anonymity
1. VPN
Traffic Encryption:
- Protocols: VPNs use encryption protocols such as OpenVPN, IKEv2/IPsec, and WireGuard. Encryption algorithms include:
- AES-256-CBC or AES-256-GCM for symmetric encryption.
- RSA-2048 for asymmetric key exchange.
IP Masking: VPNs mask the client’s IP address with the VPN server’s IP. This does not anonymize the user but shifts the visible IP from the ISP to the VPN provider.
Logging Policies:
- No-Logs Claims: Providers like Mullvad and ProtonVPN claim not to log user activities. Verification relies on independent audits and court cases.
- Data Exposure: VPN providers can be compelled to disclose logs if they exist, which can include connection timestamps, IP addresses, and usage data.
Traffic Analysis:
- Correlation Attacks: Analyzing traffic patterns, timing, and volume can potentially link VPN traffic to specific users, despite encryption.
Fingerprinting:
- Browser/OS Fingerprinting: VPNs do not protect you against fingerprinting. Unique device and browser characteristics (e.g., user agent, screen resolution) can still be used for fingerprinting.
2. Tor Network
Onion Routing:
- Encryption Layers: Data is encrypted in three layers, with each Tor relay removing one layer of encryption. This process ensures end-to-end encryption with the following layers:
- Layer 1: Encrypted between the client and the first relay.
- Layer 2: Encrypted between successive relays.
- Layer 3: Encrypted until reaching the exit node.
Exit Node:
- Data Visibility: Exit nodes decrypt the final layer and see the unencrypted data but cannot see the originating IP. Control of all relays is required to trace originating IP, which is theoretically and practically really costly to do.
End-to-End Encryption:
- .onion Sites: Use Elliptic Curve Cryptography (ECC) with a public/private key pair for end-to-end encryption.
3. Alternatives
I2P:
- Routing: Uses Garlic Routing, similar to onion routing but with packet encapsulation.
- Node Count: Limited nodes compared to Tor, making it less resilient to attacks.
Lokinet:
- Network Topology: Uses DHT (Distributed Hash Table) for node discovery and routing.
- Node Limitations: Smaller node network than Tor, affecting it's anonymity.
Password Security and Password Managers
Password Security
Entropy Calculation: Entropy is the randomness or unpredictability of a password, which directly affects its strength against attacks. It is measured in bits and calculated as: $$ \text{Entropy} = \log_2(N^L) $$ where:
- ( N ) = Number of possible symbols (e.g., 95 for a character set including uppercase, lowercase, digits, and symbols).
- ( L ) = Length of the password.
For example, a password of length 12 using 95 characters has:
$$ \text{Entropy} = \log_2(95^{12}) \approx 78.7 \text{ bits} $$
Passphrase Security:
-
Design and Strength: Passphrases are longer and easier to remember compared to traditional passwords. For example, “Name-Seat-Look-Chair-Plane7-Stree7” has high entropy because it combines multiple words and symbols.
The entropy of a passphrase with six words and special characters can be calculated by:
$$ \text{Entropy} \approx \log_2(W^L) $$ where ( W ) is the number of possible words (e.g., a large dictionary of words) and ( L ) is the number of words. For a passphrase with a dictionary of 10,000 words and 6 words in length:
$$ \text{Entropy} = \log_2(10,000^6) \approx 79.6 \text{ bits} $$
Big Tech Security and Privacy
Big Tech Security Measures
Security Practices:
- Advanced Security Protocols: Companies like Google and Microsoft implement good security measures, including multi-factor authentication (MFA), end-to-end encryption for specific services, and regular security audits.
- Enterprise-Level Infrastructure: These companies use enterprise-grade security technologies such as intrusion detection systems (IDS), firewalls, and advanced threat protection to protect user's data.
- Vulnerability Management: Regular patching and updates are applied to address security vulnerabilities. Bug bounty programs are often set to identify and fix security flaws.
Transparency and Trust Issues:
- Lack of Transparency: The specific details of their security implementations are not publicly disclosed, limiting the ability to fully verify their claims.
- Closed Source: Security measures and protocols are proprietary, making it difficult for independent verification and audit.
Email Security
Transport Layer Encryption (TLS)
- TLS Handshake: When an email is sent, the sending server initiates a TLS handshake with the receiving server. This handshake involves:
- Server Authentication: The receiving server presents its TLS certificate, which is verified by the sending server using a trusted Certificate Authority (CA).
- Session Key Agreement: The servers exchange a symmetric session key using asymmetric encryption to establish a secure channel. The session key encrypts following datas.
- Certificate Management: Ensures that certificates are up-to-date and valid. Misconfigured or expired certificates can lead to vulnerabilities. Tools like Let's Encrypt can automate certificate issuance and renewal.
Content Encryption
PGP (Pretty Good Privacy):
-
Key Generation: Works by creating a pair of keys (public and private) using algorithms such as RSA (Rivest–Shamir–Adleman) or ECC (Elliptic Curve Cryptography). Key lengths typically range from 2048 to 4096 bits for RSA, or 256 bits for ECC.
-
Encryption Process:
- Symmetric Encryption: The email content is encrypted with a symmetric key (e.g., AES-256). The symmetric key itself is encrypted with the recipient's public key.
- Signature: A digital signature is created using the sender's private key, allowing the recipient to verify integrity of the email.
-
Key Management: PGP requires manual exchange of public keys, often through key servers or direct exchange. Key management can be handled using tools like Gpg4win (Windows) or GpgTools (macOS).
S/MIME (Secure/Multipurpose Internet Mail Extensions):
-
Certificate Authority (CA): S/MIME relies on X.509 certificates issued by trusted CAs. These certificates include the user’s public key and are used for encryption and signing.
-
Encryption Process:
- Symmetric Encryption: Email content is encrypted using a symmetric algorithm (e.g., AES-256), and the symmetric key is encrypted with the recipient’s public key.
- Digital Signature: The sender’s private key is used to sign the email, for authentication and integrity.
-
Certificate Management: Certificates must be obtained and managed through a CA. They include public and private keys and are often stored in secure keystores or hardware security modules (HSMs).
Metadata Exposure
- Sender and Recipient Email Addresses: These addresses are visible in the email headers and can reveal communication patterns and relationships.
- Timestamps: Include sending and receiving times. These timestamps are recorded in the
DateandReceivedheaders. - Subject Line: Visible in the email headers and can provide a summary of the email’s content.
- Message-ID: A unique identifier assigned to each email message, useful for tracking.
- Return-Path: Shows where bounce messages are sent, indicating the sender’s address.
- Received Headers: Trace the path of the email through various servers, revealing server locations and potential network information.
- X-Mailer: Optional field showing the email client or software used, which can sometimes disclose information about the user’s environment.
- MIME-Version and Content-Type: The MIME protocol version and the type of content, such as
text/plainortext/html.
Minimizing Metadata Risks:
- Email Content: Avoid putting sensitive information in the subject line or body if metadata is a concern.
- Email Providers: Use services that focus on minimizing metadata leakage, such as ProtonMail or Tutanota.
Best Practices for Securing Email
- Use Encryption: Ensure that both transport layer (TLS) and content encryption (PGP/S/MIME) are properly configured and encrypted.
- Regular Certificate Updates: Keep TLS certificates up-to-date and manage encryption keys securely.
Operating Systems
Android Open Source Project (AOSP):
-
Verified Boot: Ensures that the device boots using only trusted software, preventing unauthorized modifications.
-
App Sandboxing: Apps are isolated from each other and the system, reducing the risk of malicious apps affecting other apps or system functionality.
-
Permission Management: Users can control app permissions to limit access to sensitive data and features.
-
Updates: Ensure that the device receives timely security patches. Regular updates fix vulnerabilities and improve security.
-
Rooting: Rooting can compromise security by breaking app sandboxing and granting elevated privileges to apps, making the device more vulnerable to exploits.
-
Install Custom ROMs: Consider using custom ROMs such as GrapheneOS on devices like Google Pixels.
-
Disable Unnecessary Features: Turn off or uninstall pre-installed apps and features that may collect data.
-
Keep Software Updated: Regularly update the device to ensure it has the latest security patches.
iOS:
-
Closed Source: iOS is not open-source, which limits the ability to audit its source code for vulnerabilities.
-
Security Features: Includes app sandboxing, data encryption, and secure boot. Apple controls app distribution through the App Store, reducing the risk of malicious apps.
-
Limited Customization: Users have limited ability to alter core settings or install third-party software outside the App Store.
-
Data Collection: Apple collects a lot of user data.
-
Review Privacy Settings: Regularly check and adjust privacy settings to limit data sharing and access.
-
Keep iOS Updated: Ensure that the device runs the latest version of iOS to have latest security patches.
-
Use Strong Passcodes: Use strong passcodes and enable two-factor authentication to increase device security.
Windows:
-
Telemetry Data: Windows collects telemetry data, which may include information about system usage and errors.
-
Closed Source: Windows source code is not open for public review, making it harder to detect and fix vulnerabilities.
-
Zero-Day Vulnerabilities: Because Windows is closedsources it means that vulnerabilities can exist before they are discovered and patched.
-
Privacy Settings: Windows offers settings to control privacy and data collection, but these settings cannot not fully prevent data sharing.
-
Consider Linux: For enhanced security and privacy, consider using a Linux distribution for regular tasks and only use Windows in a virtual machine if absolutely necessary.
-
Adjust Privacy Settings: Configure privacy settings to limit data collection and sharing with Microsoft.
-
Use Security Tools: Use additional security tools, such as firewalls to protect the system.
Linux:
-
Open Source: The open-source nature of Linux allows for bugs and vulnerabilities to be found sooner than Windows, reducing the risk of unpatched vulnerabilities.
-
Customization: Users can choose from thousands of distributions and variations of the Linux kernel.
-
Kernel Variations: Specialized kernels like linux-hardened include extra security features to enhance system protection.
-
Select a Security-Focused Distribution: Choose distributions like Qubes OS or Whonix for more security and privacy features.
-
Regular Updates: Keep the system and software updated to protect against known vulnerabilities.
Encryption
Cryptographic Analysis: Validated algorithms gone through extensive cryptanalysis, including:
- Differential Cryptanalysis: Analyzes how differences in input affect differences in output.
- Linear Cryptanalysis: Uses linear approximations to describe the behavior of the encryption algorithm.
- Algebraic Attacks: Exploits algebraic structures in the cryptographic algorithm.
- Sieve Attacks: Finds solutions to equations used in cryptographic schemes.
Example Algorithms:
- AES: Operates on 128-bit blocks with 10, 12, or 14 rounds of processing, using SubBytes, ShiftRows, MixColumns, and AddRoundKey operations.
- ChaCha20: A stream cipher with 20 rounds of processing, using a quarter-round function for high-speed encryption.
The Encryption Pitfalls:
- Security Through Obscurity: Algorithms should be secure based on their design and resistance to cryptanalysis, not on secrecy.
Techniques to prevent some implementation attacks:
- Constant-Time Algorithms: Implementations that ensure constant execution time, can reduce the risk of timing attacks.
- Noise Generation: Uses randomness to mask power consumption patterns.
Hardware Performance Factors:
- AES-NI: Hardware acceleration for AES encryption, improving performance with modern CPUs.
- TPM: Provides hardware-based protection for cryptographic keys, ensuring they are not exposed even if the system is compromised.
Backups
Backup Technologies:
- RAID Levels:
- RAID 1: Mirroring for redundancy.
- RAID 5/6: Striping with parity for data redundancy.
- Snapshot Technologies:
- ZFS Snapshots: Efficient point-in-time copies of data.
- LVM Snapshots: Logical volume snapshots for incremental backups.
Encryption Tools:
- VeraCrypt: Provides both container and volume encryption.
- Cryptsetup: Utilizes LUKS (Linux Unified Key Setup) for disk encryption.
Advanced Anonymity Techniques and Tools
- VPN Usage
- Multi-Hop VPN: Combining multiple VPN servers in different countries to add layers of obfuscation. Services like ProtonVPN offer this feature.
- Onion Over VPN: Routing your VPN traffic through the Tor network for added security. This can be set up on some VPN providers’ platforms.
- Secure Operating Systems
- Qubes OS: Offers security through virtualization. Each application runs in a separate virtual machine, which limits the impact of any potential bad code.
- Whonix: Uses a split-design where the Tor gateway and the workstation are isolated to enhance security.
- Secure Communication
- PGP (Pretty Good Privacy): For encrypting emails and files. The OpenPGP standard can be used with email clients like Thunderbird with the Enigmail plugin.
- GPG (GNU Privacy Guard): An open-source implementation of PGP. It's widely used for encrypting data and communications.
- Metadata Removal
- MAT2 (Metadata Anonymisation Toolkit): A toolkit for removing metadata from files in batch. Useful for handling multiple files at once.
- ExifTool: A command-line tool for removing metadata from various file types, including images and documents.
- Data Encryption
- VeraCrypt: For encrypting data stored on your devices. It allows creating encrypted virtual disks and encrypting entire partitions.
- EncFS: A FUSE-based filesystem that transparently encrypts files.
- Behavioral Analysis Tools
- Keystroke Dynamics: Tools like KeyTracer can help analyze typing patterns, and avoiding these patterns can enhance anonymity.
- Mouse Gestures: Tools that randomize mouse movement or use scripts to obfuscate typical mouse patterns.
- Network Security
- DNS-over-HTTPS (DoH): Encrypts DNS queries to protect against eavesdropping and tampering. Supported by browsers like Firefox and Chrome.
- DNS-over-TLS (DoT): Another encryption method for DNS queries, supported by many VPNs and network configurations.
- Data Sanitization
- BleachBit: An open-source tool for cleaning up disk space and removing traces of activities.
- CCleaner: For Windows users to clean temporary files and system traces.
Appendix B
Additional Resources for Chaper 1:
Books
-
"Nothing to Hide: The False Tradeoff Between Privacy and Security" by Daniel J. Solove
- Breaks down why the idea that privacy and security are at odds is a total myth.
-
"The Age of Surveillance Capitalism" by Shoshana Zuboff
- Looks at how big tech companies are cashing in on our personal info and what that means for us.
-
"The Transparent Society" by David Brin
- Talks about how being open and being watched affects us, and how to keep a balance between the two.
-
"VPNs Illustrated: Tunnels, VPNs, and IPsec" by Jon C. Snader
- A book covering the details of VPN technologies, including IPsec and other tunneling methods.
-
"Network Security Essentials: Applications and Standards" by William Stallings
- Covers the basics of network security, including important apps and standards to keep your data safe.
-
"Applied Network Security Monitoring: Collection, Detection, and Analysis" by Chris Sanders and Jason Smith
- A guide on how to monitor your network for security threats, from collecting data to spotting and analyzing attacks.
RFCs:
-
RFC 2401 - Security Architecture for the Internet Protocol: Explains the basic framework for IPsec, a bunch of protocols to secure internet communications.
-
RFC 4301 - Security Architecture for the Internet Protocol: An updated guide to IPsec, outlining how its security features work together.
-
RFC 1826 - IP Authentication Header: Talks about the IP Authentication Header (AH) for ensuring data integrity and confirming where data comes from.
-
RFC 4507 - Transport Layer Security (TLS) Session Resumption without Server-Side State: Describes how to resume TLS sessions efficiently, which is useful for VPNs that use TLS.
-
RFC 4306 - IKEv2: The Internet Key Exchange Protocol Version 2: Details how IKEv2 handles key exchanges, a key part of many VPN setups.
Online Technical Guides and Resources:
- Cisco’s VPN Protocols Overview
- Detailed information about VPN protocols and technologies.
- OpenVPN Protocol Documentation
- In-depth details about the OpenVPN protocol, including its configuration and security features.
- WireGuard Protocol Documentation
- Official documentation for WireGuard, a modern and efficient VPN protocol.
- TLS/SSL Protocol Overview
- Information on the Transport Layer Security (TLS) protocol, which is used in some VPNs for encrypting data.
Additional Resources for Chapter 2:
BOOKS:
-
Threat Modeling: Designing for Security by Adam Shostack
- A guide to threat modeling.
-
Security Engineering: A Guide to Building Dependable Distributed Systems by Ross Anderson
- In-depth exploration of security engineering principles.
-
The Art of Invisibility by Kevin Mitnick
- Practical strategies for maintaining privacy online.
MANUALS & SPECIFICATIONS:
- OWASP Threat Modeling Cheat Sheet : Practical guidance for threat modeling.
Additional Resources for Chapter 3:
BOOKS:
-
Data and Goliath: The Hidden Battles to Collect Your Data and Control Your World by Bruce Schneier
- Breaks down how big companies collect your data and why it matters.
-
Privacy and Security for Online Accounts by David A. Chappell
- How-to guide for protecting your online accounts and staying safe online.
RFCs:
-
RFC 6750: The OAuth 2.0 Bearer Token Usage: Specification for secure token usage in OAuth 2.0.
-
RFC 7231: Hypertext Transfer Protocol (HTTP/1.1): Semantics and Content: Details HTTP and how to secure data transmission.
Additional Resources for Chapter 4:
MANUALS & SPECIFICATIONS:
- PGP (Pretty Good Privacy) User Guide: Instructions for using PGP to encrypt email content.
- Tor Project: Tor Browser Manual: Guide to using the Tor Browser.
- ProtonMail Security Practices: Documentation on ProtonMail's encryption practices and security features.
- Diceware Passphrase : Guide for generating secure Diceware passphrases.
Additional Resources for Chapter 5:
BOOKS:
-
"Applied Cryptography: Protocols, Algorithms, and Source Code in C" by Bruce Schneier
- All about cryptographic algorithms and how to use them in code.
-
"Cryptography and Network Security: Principles and Practice" by William Stallings
- Deep dive into how cryptographic techniques keep data secure.
-
"Introduction to Modern Cryptography: Principles and Protocols" by Jonathan Katz and Yehuda Lindell
- Basics of modern cryptography and how it works.
-
"Practical Cryptography for Developers" by Svetlin Nakov
- Guide for using cryptography in software development.
-
"The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography" by Simon Singh
- Cool history of cryptography and its development over time.
TECHNICAL DOCUMENTS:
- NIST Special Publication 800-38A: Recommendation for Block Cipher Modes of Operation: Technical details on block cipher modes and their usage.
- NIST Special Publication 800-175B: Guide to Secure Use of Cryptographic Algorithms: Practical guide on the secure use of cryptographic algorithms.
Additional Resources for Chapter 6:
BOOKS:
-
"Privacy and Data Protection in the Age of Big Data" by L. Westin
- Explores the intersection of privacy, data protection, and new technologies.
-
"The Privacy Engineer's Manifesto" by Michelle Finneran Dennedy
- Talks about privacy engineering and practices for protecting personal data.
MANUALS AND SPECIFICATIONS:
- RFC 6454: The "Same-Origin" Policy: Details the Same-Origin Policy which is critical in understanding web security and fingerprinting.
- Canvas Fingerprinting: Specification for HTML5, including Canvas API used in fingerprinting.
- WebGL Specification: Details of WebGL API used for fingerprinting.
- AudioContext API Specification: Describes the AudioContext API used in audio fingerprinting.
- Tor Project Documentation: Official documentation for Tor Browser and its features for anonymity.
Additional Resources for Chapter 7:
MANUALS AND SPECIFICATIONS:
- Tails User Manual: A guide for using the Tails operating system.
- Whonix Documentation: Official documentation for setting up and using the Whonix OS.
- Tor Project’s Tor Browser Manual: Guide to using the Tor Browser.
- Qubes OS Documentation: Guide on using Qubes OS.
Acknowledgements
This book was a mess, is a mess, and will be a mess because I refused to use AI to write it. The content and structure are poorly written by me. I am not a writer, not a native English speaker, and I have no idea what I am doing (in terms of writing a book, of course). But this book is not AI-free; I have used AI only and ONLY to fix my grammar mistakes (where I don’t have that many, to be honest) and my misspellings. Although the AI might have decided that my human mind’s vocabulary is not complex enough for the readers of this book and changed them (which are fixed and rewritten in the review), I would rather write a poorly structured book, with the vocabulary of a 10-year-old, than have it written by a soulless algorithm, as everything is nowadays. So AI has been ONLY a tool to fix grammar and misspellings of this book; it has had no influence on the content, structure, wordings, and tone. If it is bad, that is my fault, and I take full responsibility for it.
Writing this book wouldn't have been possible if it weren’t for those boring classes I had to take at the university last term. The boredom they gave me made me start the book that I had wanted to start for years, and for the moral support of the good friends who stood by me and wish to remain unnamed.
I would like to thank all the good people at Techlore, PrivacyGuides, and PrivSec, from whom I learned a lot, and some of whom were really good friends, although they might not know me by this name. They do a great job at informing people about privacy and security and providing up-to-date and well-selected guides on privacy and security.
Most of the content of this book is from a period of fear and paranoia that took over my life in the middle of 2020, which was probably due to COVID and isolation, but it made me go crazy about privacy and anonymity, and most of my knowledge comes from those not-so-pleasant days of my life. Although learning and implementing these privacy practices weren’t pleasant at the time, sharing them definitely was, and I’m glad that I did so.
Donations and Support
This book is free and open source and will stay free and open source because what's important to me is that it is read and comes in useful. I’m not looking for profit, but I can't deny that every donation, no matter the amount, or even an appreciation email, allows me to put more time into projects like this.
So here are every cryptocurrency I could think of. If you would like to donate, here are the ways to do so:
-
Monero (XMR):
8AF4Lybz7QwiucdYW2szsgiqTHdBp5kjZSSRm6ddzd5363S6n4jixpkACGMLx5JWZnUR5MnGF7cMoidjppruAvLvMe2ovHZ -
Zcash (ZEC):
t1WbpyRF7sXidefAzA5Vb922dsR3PLe9bRZ -
Bitcoin (BTC):
bc1qdzdlytujxn3l02vdt90xx5pkqlezxpuucs6fmm -
Ethereum (ETH):
0x9E00DC6bE0d07bDB5Ff8B62593a0193913c9B595 -
Bitcoin Cash (BCH):
qzmxuv82j9n2zlxkylrz882yk9e50wvzz5a6hqy2dc -
Dash:
XamhGMK5XM1wPKqSiF8HACJsToVmW4jMGL -
Dogecoin (DOGE):
DBEaZAbo5tDk7LuXd7pCkhQMa2h8kBgVbS -
Litecoin (LTC):
ltc1qrex5xq3px5qn9vjplfkmvzf7sweks3r4skxe5k -
Matic (MATIC):
0x9E00DC6bE0d07bDB5Ff8B62593a0193913c9B595 -
TON :
EQAjMitBSLjcl4DwthElddvuRSW3N-Dvd0HX-RkGMUVsC9sT -
TRON (TRX):
TUT762nFQQRoXvDe1Z72p3kKH9uY3XZCg9 -
Stellar (XLM):
GDT7GJS6U3N2CCWNQAORW2EJ2XFDCUGXOGZXEMGKOP6ILQ77ZIPN3ET4 -
Cosmos (ATOM):
cosmos1pwu953l57000n9hleerzm3hzaclldhpxf86l32 -
Solana (SOL):
5TT1URTgmnXziXXS1avgV4uF7Dwj5f3MNHLPcZtQKVk9 -
Ravencoin (RVN):
RLN8CqRzgDajY77Sd3xYREVLheTYEb7rWc
Or if you want to send it another way, or you want to let me know of your donation or just have something to say, please feel free to email me at zolagonano@protonmail.com. I appreciate every donation and message, and they really help me put more time into the things I like.